CrowdStrike insider trading has recently caught the attention of market watchers and regulators alike. This cybersecurity company, known for its advanced threat detection and response capabilities, finds itself in the spotlight due to a notable stock sale by a high-ranking executive.
CrowdStrike insider trading activity took center stage when the company’s Chief Security Officer, Shawn Henry, sold 4,000 shares on July 15, 2024. The sale, totaling approximately $1.485 million, comes just days before a global IT outage that affected CrowdStrike’s operations and stock price.
The sale was executed under a prearranged 10b5-1 trading plan, a mechanism designed to prevent insider trading by allowing company insiders to set up predetermined stock sale schedules.
CrowdStrike insider trading casts a long shadow
The proximity of this CrowdStrike insider trading event to the subsequent IT issues has drawn considerable attention. On July 19, 2024, CrowdStrike experienced a widespread service disruption stemming from an update to its Falcon cybersecurity platform. This outage caused the company’s stock to plummet, closing at $304.36 – an 11% decrease from the previous day’s value.
The sharp decline in stock price following the CrowdStrike insider trading and IT outage has interrupted the company’s strong performance in 2024. Before these events, CrowdStrike’s stock had seen impressive gains of over 20% throughout the year.
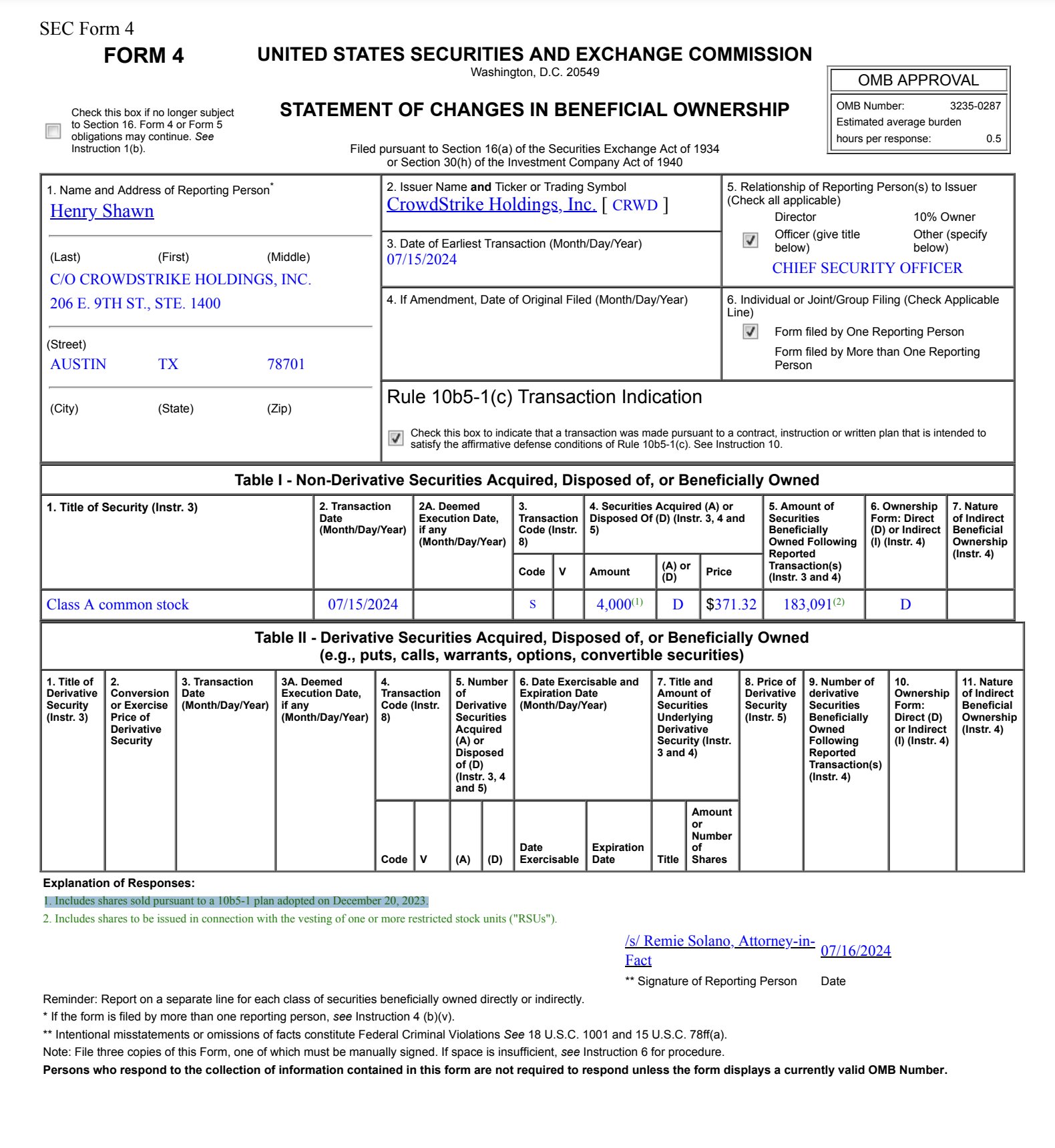
The CrowdStrike insider trading case presents a complex scenario for regulators and shareholders to examine. While the use of a 10b5-1 trading plan suggests a predetermined nature to the stock sale, the timing remains a point of interest.
However, the proximity of the sale to the IT outage has led some to question whether there might have been any knowledge of potential issues before the public announcement. It’s important to note that no evidence has been presented to suggest any wrongdoing, and the use of the 10b5-1 plan provides a layer of protection against such allegations.

What else has happened or will happen?
Let us give you a summary and brief information about what may happen in the future.
- The recent IT outage, caused by an error in an update for Windows hosts, has impacted sectors such as travel, banking, retail, and healthcare. CrowdStrike, warns of scammers and hackers exploiting the situation. The Cybersecurity and Infrastructure Security Agency (CISA) has commented on the ongoing malicious activity, including phishing attempts. The agency is working closely with CrowdStrike and other private sector and government partners to monitor any emerging malicious activity. Users must be extra vigilant when dealing with emails and messages, especially if they encourage downloading or clicking on links.
- Microsoft has released a recovery tool to assist IT admins in repairing Windows machines affected by CrowdStrike’s Blue Screen of Death error. The tool creates a bootable USB drive, allowing IT admins to quickly recover affected machines without manually booting into Safe Mode or deleting the problematic CrowdStrike update file. The tool also offers recovery steps for Windows Virtual Machines running on Azure and all Windows 10 and Windows 11 devices.
- CrowdStrike’s Falcon Sensor software has been linked to Linux kernel panics and crashes, causing widespread outages of Windows-powered computers. Red Hat warned its customers of a problem affecting some users of Red Hat Enterprise Linux 9.4 after booting on kernel version 5.14.0-427.13.1.el9_4.x86_64. CrowdStrike is also suspected of causing problems in Debian and Rocky Linux. Linux kernel panics and Windows Blue Screens of Death are broadly comparable, and the occurrence of kernel panics mere weeks before CrowdStrike broke many Windows implementations hints at wider issues at the security vendor.
The repercussions of the CrowdStrike insider trading and subsequent IT outage extend beyond the company itself. Many of CrowdStrike’s customers experienced service interruptions due to the Falcon platform update. The malfunction affected interactions with other systems, including Microsoft’s Windows products, effectively disabling these systems and widely used software globally.
Featured image credit: Austin Distel / Unsplash