On one hand, we see a very popular video chat software, on the other hand, growing concerns about security and privacy; this brings one question to one’s mind: Is Zoom secure?
Zoom has increased the number of daily meeting users from 10 million in December 2019 to 300 million in April 2020. With this huge interest, we wanted to ask some of the questions that comes to everybody’s mind to Emrah Aydin, Marketing Manager, Zoom Video Emerging Markets.
 Security researchers announced that personal information were shared with third parties such as Facebook. What did you do about this?
Security researchers announced that personal information were shared with third parties such as Facebook. What did you do about this?
We take our users’ privacy extremely seriously, and we’ve taken action to address this issue — for more information, please see our blog post here.
We originally implemented the “Login with Facebook feature” to provide our users with another convenient way to access our platform. When we learned the Facebook SDK was collecting device information unnecessarily, we decided to remove the Facebook SDK in our iOS client. Importantly, the information collected by the Facebook SDK did not include information and activities related to meetings but rather information about devices such as the mobile OS type and version.
There were personal information of 500K Zoom users on the dark web. Did we get our data stolen by using Zoom?
It is common for web services that serve consumers to be targeted by this type of activity, which typically involves bad actors testing large numbers of already compromised credentials from other platforms to see if users have reused them elsewhere.
This kind of attack generally does not affect our large enterprise customers that use their own single sign-on systems. We have already hired multiple intelligence firms to find these password dumps and the tools used to create them, as well as a firm that has shut down thousands of websites attempting to trick users into downloading malware or giving up their credentials.
We continue to investigate, are locking accounts we have found to be compromised, asking users to change their passwords to something more secure, and are looking at implementing additional technology solutions to bolster our efforts.
Additionally, during Zoom’s “Ask Eric Anything” webinar on 4/15, Alex Stamos offered a thorough overview of Zoom’s approach to identifying and mitigating instances of account credentials sold on the dark web. For more information on how this is done, a recording of the webinar can be found here – with discussion of this issue beginning around the 32:29 mark.
- Zoom does not sell our users’ data.
- Zoom has never sold user data in the past and has no intention of selling users’ data going forward.
- Zoom does not monitor your meetings or its contents.
- Zoom complies with all applicable privacy laws, rules, and regulations in the jurisdictions within which it operates, including the GDPR and the CCPA.
- We are not changing any of our practices. We are updating our privacy policy to be more clear, explicit, and transparent.
Zoom takes its users’ privacy extremely seriously. Zoom collects only the data from individuals using the Zoom platform required to provide the service and ensure it is delivered effectively under a wide variety of settings in which our users may be operating.
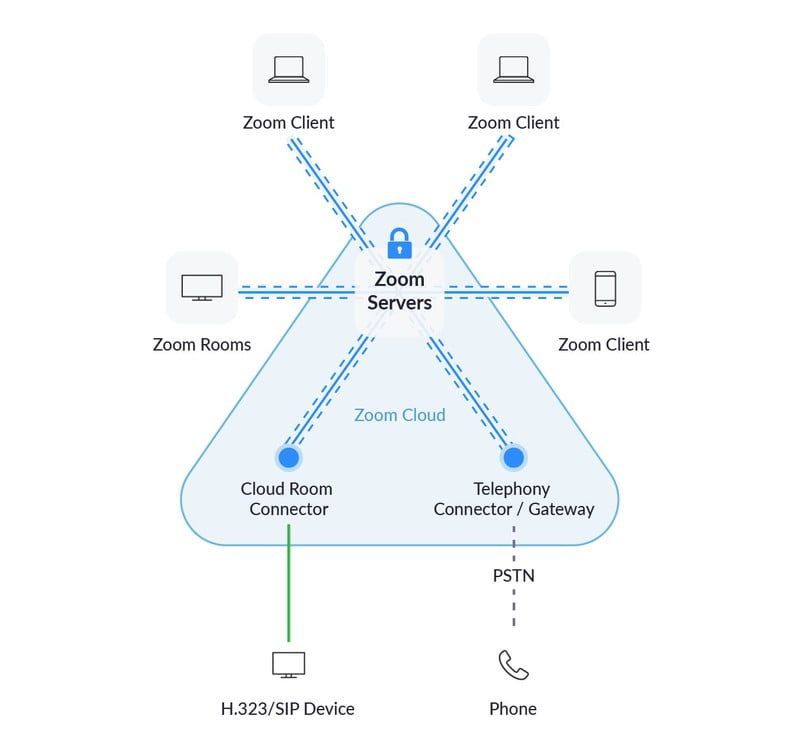
Does Zoom encrypt our meetings or not?
Information on Zoom’s encryption practices can be found in this blog post and in this encryption paper. Importantly, all video, audio and chat content is encrypted the entire time it is transiting the Zoom system.
The new Zoom 5.0 supports AES 256-bit GCM, one of the most secure encryption standards used today, positioning Zoom as an industry leader with regards to encryption security for open and interoperable video communications at scale. Zoom does plan to offer end-to-end encryption for its meetings at some point in the future and the company provided an update on this during the April 15th weekly webinar. Please see the full recording here – with discussion of this issue beginning around the 39:42.
What to do in order to not experience a Zoombombing incident?
We have been deeply upset to hear about these types of incidents. Zoom strongly condemns such behavior and recently updated several features to help our users more easily protect their meetings.
We have enabled meeting passwords and virtual waiting rooms by default for users enrolled in our K-12 program, as well as our Free Basic and Single Pro users. For users enrolled in our K-12 program, we have also updated the default screen share settings to ensure teachers are the only ones who can share content in class.
For all users, we have made the Zoom Meeting ID less visible to help prevent unintended sharing, and we have added a new Security icon to the Zoom meeting controls for all hosts to help them quickly access in-meeting security features, including the ability to remove participants and lock meetings, among other actions. In the latest version of Zoom, there is a new ‘Report a User’ feature in the Security icon for meeting hosts and co-hosts to flag users, who are misusing the platform, to our Trust & Safety team.
- Zoom published on April 12 a document containing the best practices for securing Zoom meetings.
- Zoom tweeted on April 10 a graphic that outlined the top 10 ways for users to secure their Zoom meetings.
- Zoom blog posted on April 8 the recently implemented security updates to make meetings more private and secure.
Zoom blog posted on March 20 with guidance for users on how to prevent uninvited guests from joining Zoom meetings.
Is Zoom a Chinese company? Do our data pass through China and should we be worried about this?
Zoom is an American company, publicly traded on the NASDAQ and led by an American citizen, with headquarters in San Jose, California and offices around the globe. All Zoom source code is stored and versioned in the United States.
Zoom’s software developers in China are largely managed by our engineering team in the United States and they carry out their responsibilities in accordance with the design and architecture decisions made by Zoom’s U.S. Engineering group.
These developers in China do not have any access to Zoom’s production environment, the power or access to make substantive changes to our platform or the means to access any meeting content. And, importantly, across all of Zoom engineering, regardless of location, our engineers only have access to the source code required for their particular function.
Zoom leverages a robust global network to support our users, both free and paid, natively routing traffic through the meeting zone that will provide the best performance. While recent changes provide additional optionality for Zoom’s paid customers, free users will continue to be supported by data centers within their default geographic region where their account is provisioned, with additional geofencing best practices still enforced.
There were companies and governments banning Zoom and some also warned about the use. What are you doing in regard to these actions?
We are in communication with government offices and focused on providing the information they need, including about our tailored Zoom for Government offering, which is hosted in a separate cloud and meets the particular specifications of FedRAMP security policies, to make informed decisions about their policies.
A large number of global institutions ranging from the world’s largest financial services companies, to leading telecommunications providers, government agencies, universities and others have done exhaustive security reviews of our user, network and datacenter layers and confidently selected Zoom for complete deployment.
Zoom takes user security extremely seriously and is providing regular updates on the steps we are taking to further strengthen our platform.
There is also an allegation that there is a malware that can record Zoom meetings unknown to the hosts and participants. What do you think about this?
This is an attack vector that all Windows applications are susceptible to – not just Zoom. Executing this attack as described requires a user to self-install a piece of malware to their own computer. Once running, that malware can, like any other piece of malware, control and alter the behavior of any locally-executed applications, including Zoom.
Zoom has a fast growing user base, how long can your systems can endure this?
All of our services are currently fully operational – you may refer to our status page https://status.zoom.us for the latest updates.
We are confident that our architecture is built to handle these growing levels of activity. Our unified communications platform is architected from the ground up to address the most technologically difficult aspect of communications: video. Specifically:
- We operate our own global (co-location) data centers in 17 locations around the globe, providing significant control and flexibility when it comes to routing both our audio and our video traffic.
- We have architected the platform such that, in the event of capacity constraints at the data center nearest a user, additional traffic will be routed to one of our other data centers.
- In the case of an unprecedented, massive influx of demand, we have the ability to access and deploy tens of thousands of AWS servers within hours, and in full compliance with our Privacy Policy, to seamlessly scale without any impact to our users.





