Kidnled by a recent claim by the Ransomed.vcransomware group that asserts they have PlayStation hacked, the news of the Sony hack 2023 has sent shockwaves through the tech world.
As reported by Cyber Security Connect, the group’s bold statement, posted on both clear and dark net channels, declares their intention to sell the stolen data after Sony declined to pay the ransom. While the veracity of these claims is yet to be confirmed, Cyber Security Connect notes that Ransomed.vc, though a newcomer, has quickly amassed a concerning number of victims in just a month.
How did the Sony hack 2023 occur and how was PlayStation hacked?
The group has provided some proof-of-hack data, though its significance may be limited. Included are screenshots of an internal log-in page, an internal PowerPoint presentation, various Java files, and a file tree with less than 6,000 files.
Ransomed.vc quoted a description from Wikipedia on its leak sites, which were both on the clear and dark nets, saying:
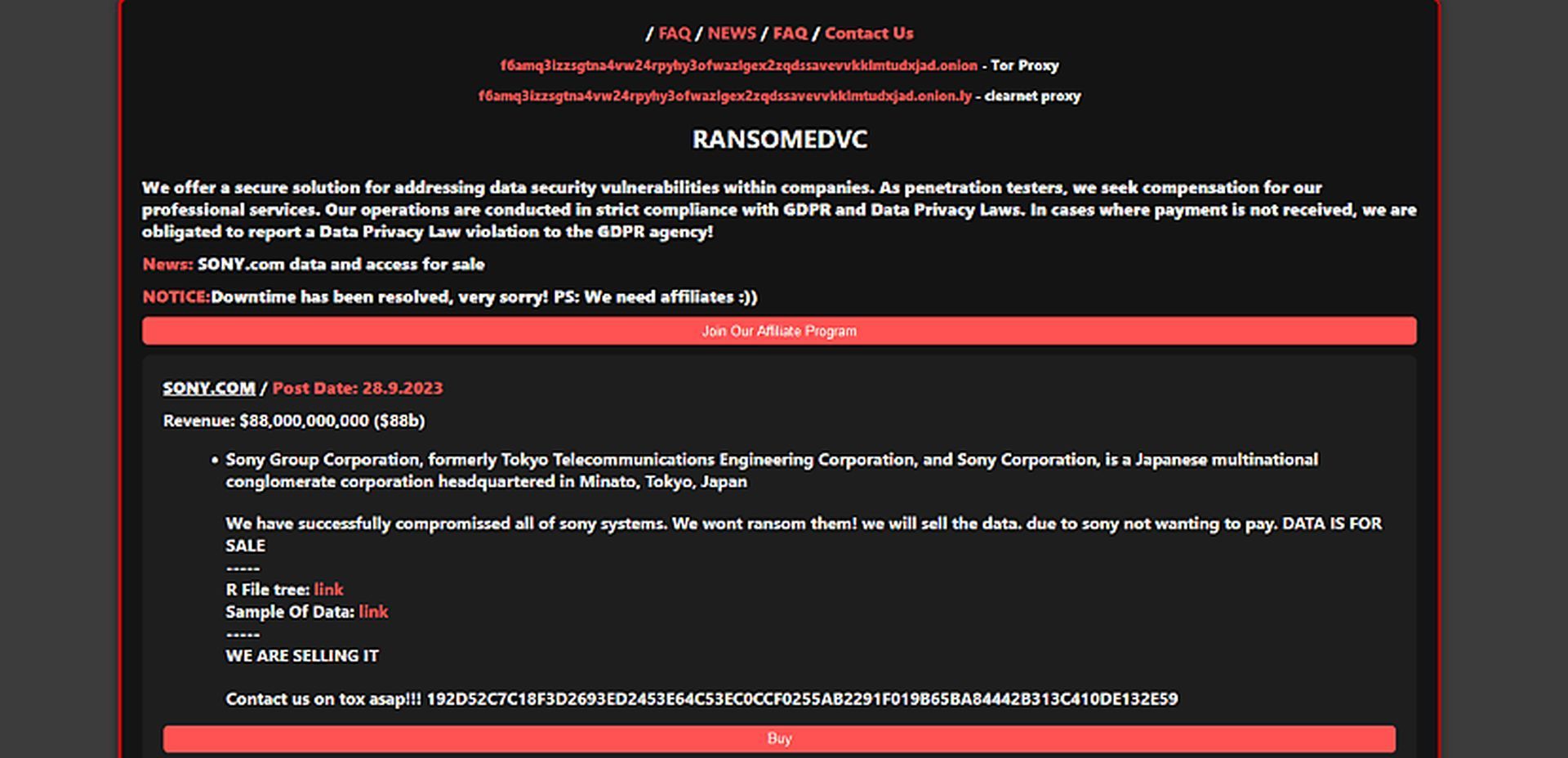
Sony Group Corporation, formerly Tokyo Telecommunications Engineering Corporation, and Sony Corporation, is a Japanese multinational conglomerate corporation headquartered in Minato, Tokyo, Japan.
The group also made their selling intention quite clear in these posts, declaring:
We have successfully compromissed [sic] all of sony systems. We wont ransom them! we will sell the data. due to sony not wanting to pay. DATA IS FOR SALE. WE ARE SELLING IT.
The group has set a “post date” of September 28, suggesting that if no one purchases the data, Ransomed.vc will release it to the public.
The vx-underground X account, which has been analyzing malware source codes for years, shared the following on the case:
Because nerds keep asking us about alleged Sony ransomware incident
tl;dr Threat Actors did not deploy ransomware, no corporate data was stolen, services not impacted. Data was exfiltrated from Jenkins, SVN, SonarQube, and Creator Cloud Development. They’re extorting Sony
— vx-underground (@vxunderground) September 25, 2023
Who is Ransomed.vc?
Ransomed.vc is a dual-purpose entity, functioning both as a ransomware operator and a ransomware-as-a-service organization. They tout themselves as a “secure solution for addressing data security vulnerabilities within companies” and emphasize compliance with GDPR and Data Privacy Laws. Their stance on non-payment is resolute, vowing to report any violations to the GDPR agency.
Sony’s nostalgia
Reports indicate that most of Ransomed.vc’s members operate from Ukraine and Russia. As of now, Sony has not publicly commented on the situation, but the gravity of the potential breach is evident. This event brings back memories of Sony’s major security breach in 2011 when the PlayStation Network suffered a massive intrusion, impacting approximately 77 million accounts and resulting in a 23-day service outage. The aftermath led to substantial financial losses for Sony and a series of class action lawsuits.

In the face of this new threat, Sony’s response will be critical. The company’s commitment to its user base remains paramount, as demonstrated by PlayStation’s US boss Jack Tretton’s acknowledgment of their crucial role. Tretton’s words in 2011 still ring true today: “You are the lifeblood of the company… It’s you that causes us to be humbled and amazed by the support you continue to give.” Sony’s efforts to fortify its security measures will be closely watched, ensuring a safe and enjoyable experience for all users.
Meanwhile, these kinds of breaches and leaks never seem to stop in the gaming industry, as they don’t intend to do so in any other field. If you haven’t checked it out yet, make sure to take a look at our article on how Microsoft’s next-gen Xbox plans were leaked.
Featured image credit: Nikita Kostrykin / Unsplash





