The WordPad application for Windows 10 contains a DLL hijacking vulnerability that the QBot malware operation has begun to use to infect machines while avoiding detection by security products.
A DLL is a library file that contains routines that may be utilized concurrently by many programs. An program will make an effort to load any necessary DLLs when it is started.
It does this by looking through specified Windows directories for the DLL and loading it when it is discovered. However, DLLs in the same location as the executable will be loaded first by Windows programs, taking precedence over all other DLLs.
When a threat actor creates a malicious DLL with the same name as a valid one and inserts it into the early Windows search path, often the same location as the executable, the process is known as DLL hijacking. When that executable is run, it loads the malicious DLL instead of the trustworthy one and runs any malicious instructions it finds inside.

QBot Malware steals emails for phishing attacks
Windows spyware called QBot, sometimes called Qakbot, began as a banking trojan but later transformed into a malware dropper. With the help of the malware operation, ransomware gangs including Black Basta, Egregor, and Prolock were able to first penetrate business networks and launch extortion campaigns.
ProxyLife, a security expert and member of Cryptolaemus, informed BleepingComputer that a fresh QBot phishing operation started using a DLL hijacking vulnerability in the write.exe WordPad executable in Windows 10.
Although ProxyLife informed us that the initial phishing emails include a link to download a file, BleepingComputer has not received those emails.
A random named ZIP archive from a remote site will be downloaded when someone clicks on the link.
The Windows 10 WordPad application document.exe and the DLL file edputil.dll (used for the DLL hijack) are both included in this ZIP package.
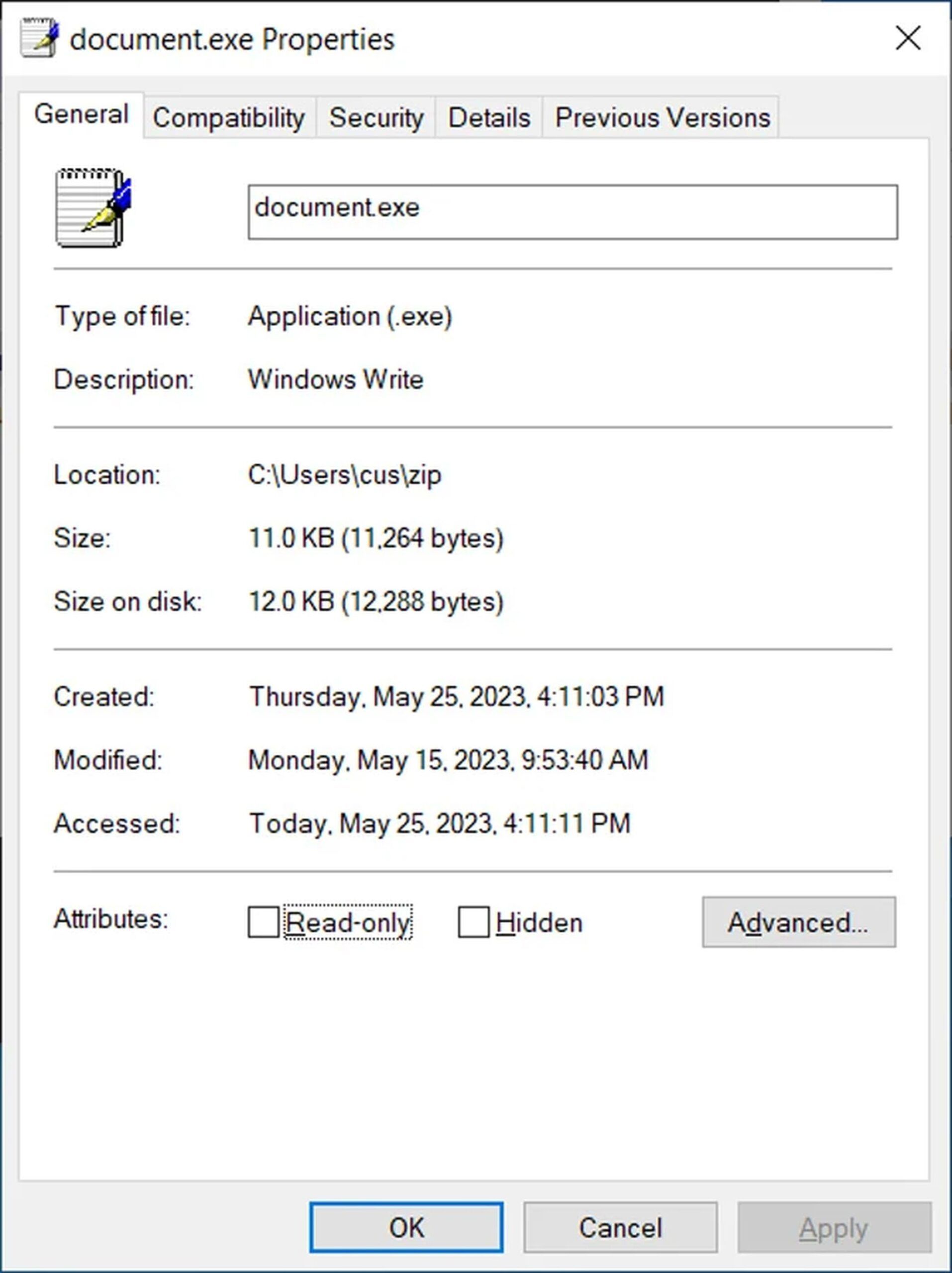
The genuine Write.exe executable used to start the Windows 10 WordPad document editor is essentially a renamed duplicate of the document.exe file, as you can see from its attributes.
A genuine DLL file named edputil.dll, which is typically found in the C:WindowsSystem32 folder, is immediately loaded when document.exe is run.
However, the executable will load any DLL with the same name located in the same location as the document.exe executable when it tries to load edputil.dll instead of looking for it in a specified folder.
Due to the creation of a malicious edputil.dll DLL and its storage of it in the same location as document.exe, the threat actors are now able to accomplish DLL hijacking.
ProxyLife informed BleepingComputer that when the DLL is loaded, the malware utilizes C:Windowssystem32curl.exe to retrieve a DLL disguised as a PNG file from a remote server.
The following command is then performed by rundll32.exe on this PNG file (which is really a DLL):
rundll32 c:\users\public\default.png,print
As Cobalt Strike (a post-exploitation toolkit threat actors employ to first acquire access to the compromised device) and other payloads are finally downloaded, QBot will continue to silently operate in the background, capturing emails for use in other phishing assaults.
Following the usage of this device as a base, the network will be infiltrated laterally, which often results in ransomware attacks and the theft of business data.

The threat actors are hoping that by installing QBot via a reputable tool like the Windows 10 WordPad (write.exe), security products will not identify the virus as harmful.
However, as previous operating system versions do not have the Curl software, employing curl.exe implies that this infection technique will only be functional on Windows 10 and later.
Since previous versions of Windows have been phased out after losing support, this shouldn’t generally be a problem. Currently, the QBot operation has switched to other infection techniques in recent weeks, although it is normal for them to revert to earlier strategies in subsequent campaigns.
If you are interested in security, we suggest that you check out Twitter phishing attacks: Verification fee’s unexpected side effects, or Battle net down Battle net DDoS attack explained (11 Oct).





