The aim of a new Facebook phishing scam, which Trustwave security experts have uncovered, is to steal user credentials by exploiting Messenger chatbots.
The chatbots in this latest Facebook phishing scam spoof the social network’s customer service representatives, according to Trustwave’s research. These bots then take control of pages by pressuring page administrators to input login information for that Facebook page. Following Trustwave’s notification, the malicious Messenger chatbots and websites were swiftly removed.
In essence, Messenger chatbots are specially created programs that act as live customer service representatives and respond to user inquiries before referring the inquiry to a human employee. Usually, companies that provide live chat or customer support services use these bots.
“The fact that the spammers are leveraging the platform that they are mimicking makes this campaign a perfect social engineering technique.”
-Trustwawe
Fake Messenger chatbots explained
This Facebook phishing scam began with an email warning the recipient that Facebook would destroy their page if they didn’t comply with community standards for Meta within 48 hours. The recipient was sent to a false Messenger support page hosted by Google Firebase when they clicked the Appeal Now link, where they had to communicate with Messenger chatbots.
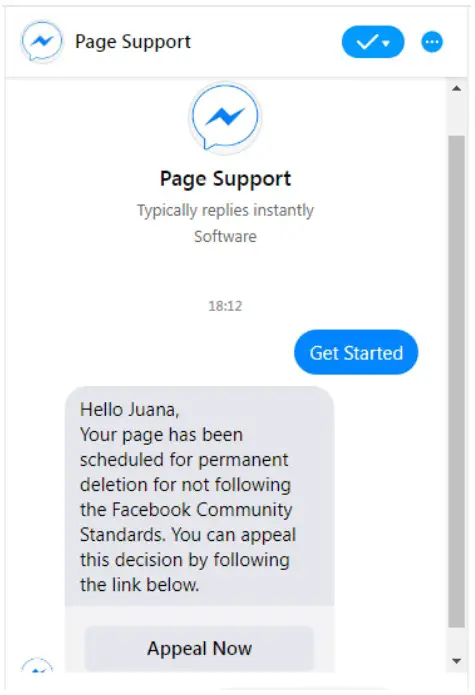
The fake Messenger chatbots act like a fan/business page with no followers or postings, as was discovered by researchers.
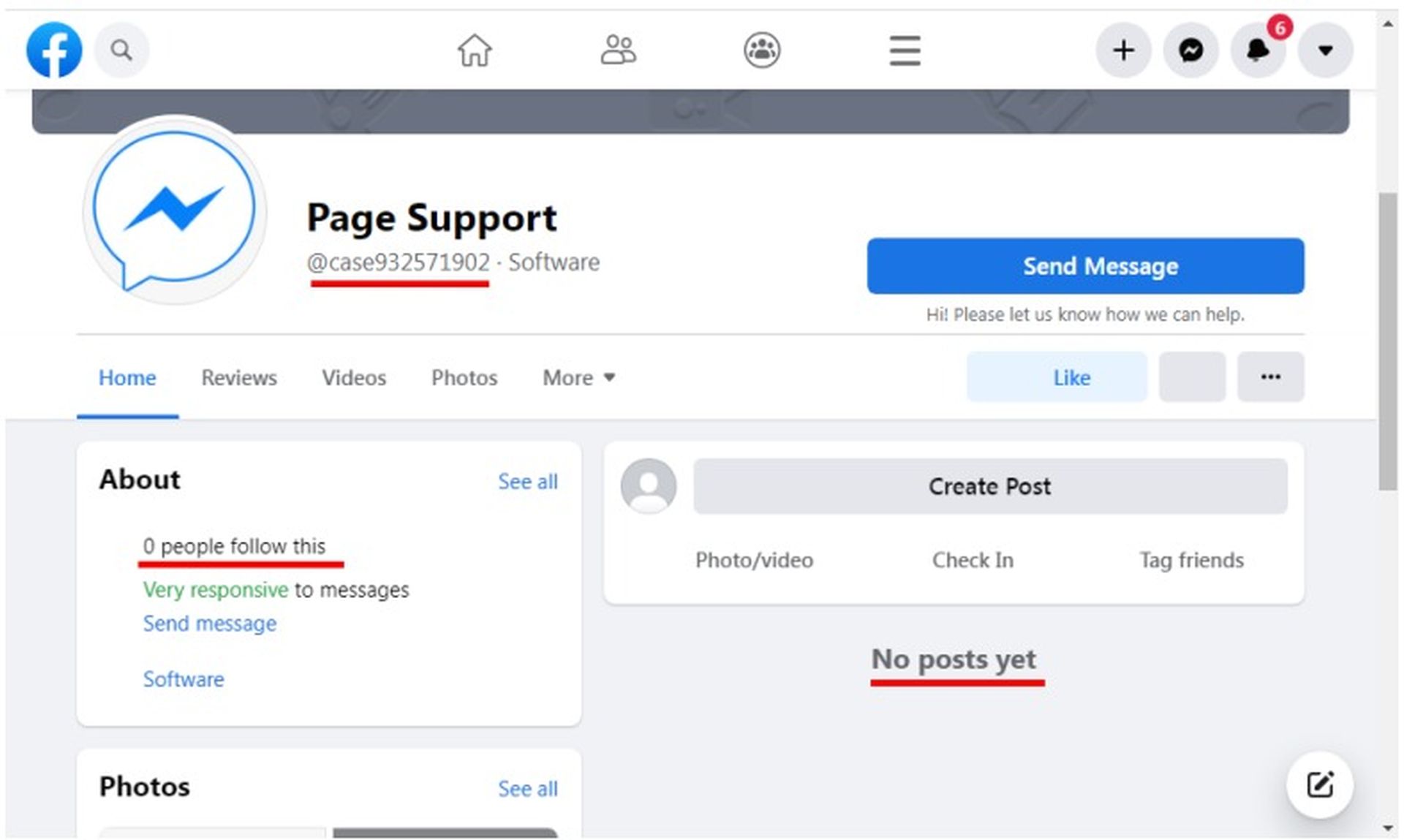
However, the attackers gave the bot the look of legitimacy by using the official Messenger logo on the profile page. The user filled out the Appeal form with their first and last names, email addresses, page names, and mobile numbers.
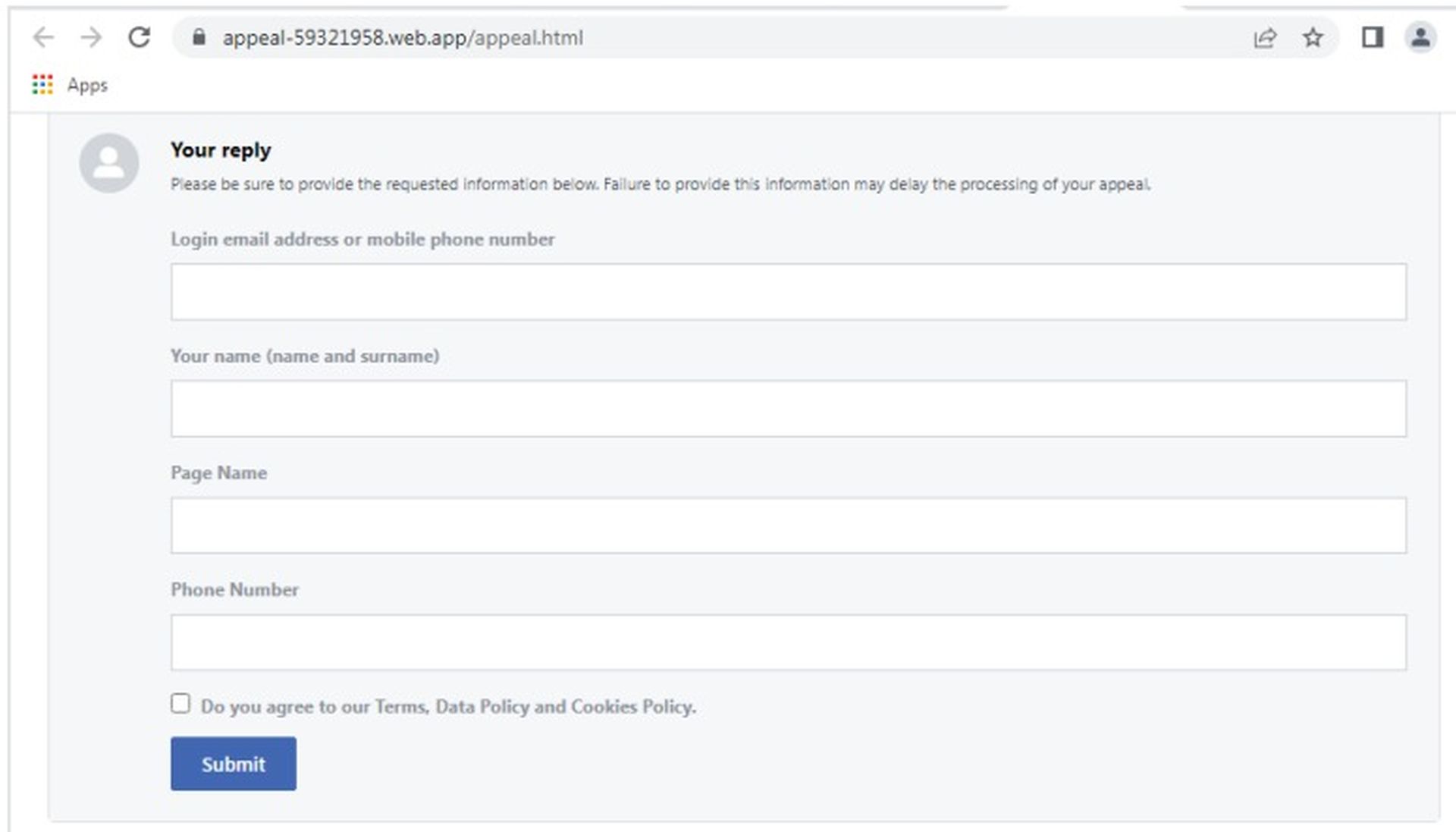
Additionally, they were prompted to perform 2FA authentication, and the length of the OTP was up to them.
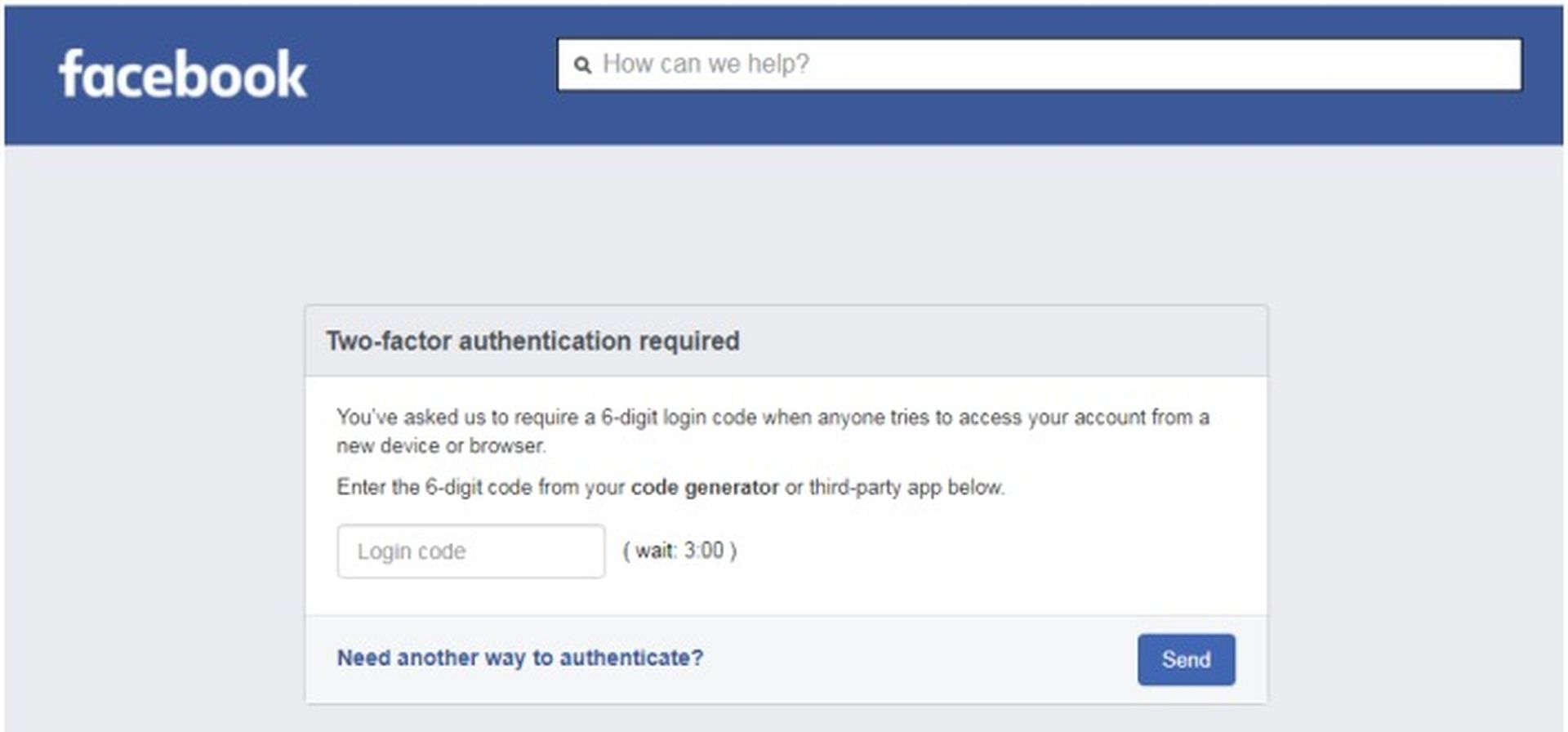
The moment the user clicked the “Submit” button, the attackers acquired the form and the user’s login information while redirecting them to Meta’s official page for intellectual property and copyright policies. Users have been facing interesting issues on Facebook, learn how to fix “No data available” Facebook error, by following the steps in our article.
How was the Facebook phishing scam exposed?
Researchers found numerous mistakes in the email that pointed to its malicious origin, which prompted suspicions. Examples include the third sentence’s missing dot and the word Page’s erroneous capitalization.
A number of mistakes in the email header further indicated the email’s fraud. For example, Policy Issues was written in the sender’s name, yet Facebook/Meta didn’t own the sender domain.
How to protect yourself from phishing attacks?
To sum up, it is crucial that social media users exercise caution when opening these warning notifications and always look for warning signs before disclosing important information. Additionally, it is always advisable to use caution while interacting with people on Facebook or other social networking platforms.
In phishing attempts, threat actors are increasingly using chatbots to automate the theft of passwords and scale up their operations without expending a lot of time or money.

These scams are more difficult to spot because many websites include AI and chatbots on their support pages, which makes them appear legitimate when users encounter them when opening support cases.
The easiest strategy to prevent phishing attempts is to always look at any URLs for pages asking for login information. If the domains don’t match the regular URL of the real site, do not enter any credentials on that page.
Don’t divulge any personal information to a user or bot if you have any doubts about their reliability, and report them to Meta instead. Be careful about this latest Facebook phishing scam in order to protect your private information and learn here how to protect personal data if your smartphone is lost or stolen.





