The friends of the unwanted are exchanging firearms for botnets to gain access to the most valuable property, usually money or cryptocurrencies. A botnet is, to simplify, a network of remotely controlled computers and, generally, with a “malicious” objective.
The term botnet comes from the English word bot (robot) and net (network). Using different protocols, computers are infected on a massive scale with a single common objective. This can be a DDoS attack, SPAM, phishing, or cryptocurrency mining.
What is a botnet?
Technically, it is a set of computers remotely controlled by a third party. While there need not be a malicious background, in most cases they are built to commit criminal acts. The creator of a botnet develops software, an application, that is able to take control of other computers remotely and autonomously without the owners of the computers themselves being aware of it. This is why terms such as “Zombies” or “Zombie Army” are also often used to refer to the set of infected computers.
Generally, a botnet executes specific commands to steal information from infected computers and analyze it. In turn, keyloggers are executed, which record all keystrokes made by the owner of the infected computer. Knowing everything typed by the user of the zombie computer, we can extract access information to all kinds of accounts such as electronic banking, online stores, etc. All this information is processed directly by the Bot Masters for their own benefit or to sell to third parties.
Botnet components
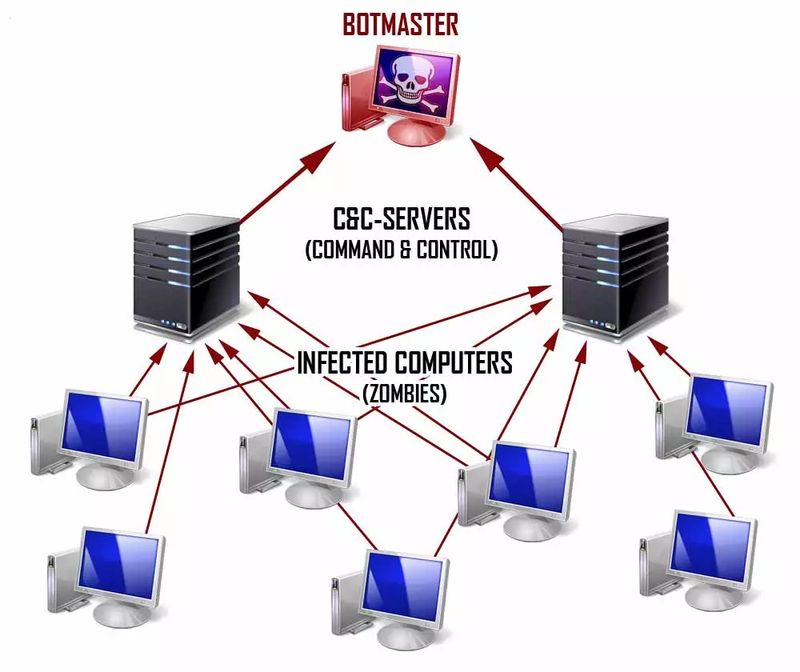
- Bot Master: Is the manager of the botnet itself. It can be the creator or not of the network and is mainly responsible for running and managing the application created specifically to manage attacks through the botnet.
- Command and Control (C&C): This is the application used by the Bot Master to communicate with all infected computers. It also allows you to launch mass actions on the infected machine.
- Zombie: This is the name given to each of the infected computers. They are usually hundreds or thousands of units.
Botnet architecture
Communication between already infected computers and new ones to be infected takes place through central servers connected to the network. A botnet accesses the servers to which the first infected PCs have connected and in turn, will continue to try to attack the rest of the computers that connect to the initial server that has been accessed. Another of the dangers that this can entail is the general crash of the network, leaving all users in a specific geographical area without service. The new botnets are mostly based on P2P protocols that do not depend on access to communication through a central server.
Expansion
Although we mostly talk about infected computers, nowadays any device connected to the network can be attacked: smartphones, smartwatches, or smart devices in general (IoT). When the botnet gains access to any of our smart devices, it connects to the rest of the computers. Once the devices are infected, they will use the usual communication channels to spread the botnet itself. The main target of hackers today is smartphones and tablets. Mobile devices accompany us everywhere and at all times, so they host all our financial information. Credit card numbers, access to online banking, and online stores are sensitive to a botnet attack.
Competition
The botnet market is huge and competition is fierce. This type of criminal activity is gaining in importance by leaps and bounds. Regardless of the business for the creators, competition has increased among the main botnet developers for the largest number of infected computers, the best quality of bots, or the fastest bandwidth.
How does a botnet infect you?
Most botnet attacks use Trojans as their primary tool. A Trojan is a harmless-looking application or executable file. It may have the icon and name of another popular application. Imagine that you receive or download a file with the Spotify icon and whose name is Spotify.exe. Many, out of ignorance or as a reflex action, double-click the file thinking they are going to update the application when in fact they are giving access to all the information on their computer and all the devices connected to the same Wifi network.
A botnet takes advantage of the communication flow between devices. In a first step, it will try to infect the other computers connected to the same Wifi network as the infected device. Then, in a second stage, it will try to find new computers connected to the same servers as the first ones. In this way the growth in the number of bots is exponential.
The same procedure is followed with “phishing”. This activity consists of sending links to Trojans without the recipient of the e-mail being aware of it. The corporate image of a financial institution is simulated, for example, and access data for electronic banking is requested. With just one individual who falls for the trap, the damage can be considerable. Nowadays, both large corporations and e-mail providers have developed various applications to control spam on SMTP servers.
Typical uses of a botnet
Botnets are the star product of the hacker business. Hackers profit from selling or renting software to create botnets that operate for their customers in different ways. Always with the aim of getting hold of confidential information of any kind or financial information.
DDoS attacks by botnets
These are Distributed Denial of Service attacks. With the help of a botnet, its developers direct attacks to web pages, forums, or digital services in general with the intention of saturating the accesses until the servers are blocked. In this way, it would be impossible to access the web page in question or the digital service that has suffered the attack.

Spam
A common practice is for a hacker to design a botnet which in turn is sold as a tool for spammers. This botnet controls hundreds or thousands of computers and their contact lists to form a giant database of email addresses. The spammer is in charge of distributing massively and without any kind of filter all kinds of unsolicited advertising communications. This activity is highly pursued by administrations and email service companies to strengthen the privacy of users.
Cryptocurrency mining
One of the most popular uses of botnets is for the generation of cryptocurrencies. This activity is based on the intensive use of many devices capable of processing mining algorithms. While it is normal to acquire and use one’s own equipment, some hackers prefer to take control of other people’s computers through botnets and make them work for them.

Cryptocurrency theft
All sensitive information is targeted by botnet developers. And financial information is the most sensitive. A botnet can be used to break into hundreds of computers and try to steal cryptocurrency access data in order to transfer it directly to the interested party.
Fake metrics
Continuing with financial information, everything related to monetization is targeted by hackers. They design botnets to control as many PCs as possible and make them click as many times as possible on specific links or advertising banners. The aim is to generate fake traffic to a website or to increase advertising revenue.
Known botnet cases
GitHub (2018)
In February 2018, a DDoS attack was perpetrated on the software development platform that rendered it inoperative for minutes. Data amounts of more than 1TB per second had been targeted.
Botnet Pony (2014)
This network managed to steal more than $220,000 in BTC from various wallets. The strategy is much simpler than one might think. By installing keyloggers, many users and access passwords were obtained.
Rustock (2006)
One of the best-known botnets. It worked continuously for five years. Designed for Microsoft Windows, it sent spam emails to all contacts found in the database of infected computers. At its peak, it sent almost 200 messages per minute from each infected computer.
How to create a botnet?
Windows and Mac OS
For the most popular operating systems, Windows and Mac OS, the usual way to infect other computers is through the installation of programs and applications. These in turn contain the code that generates the malicious actions by analyzing system vulnerabilities.
UNIX and GNU/Linux
In the open-source system environment, the way to create a botnet is developed by telnet or SSH. Both protocols control network connections and the transmission of information through them. The usual procedure is to attempt access to external computers using random users and passwords on all traced IP addresses using a scanning script running on an external server.
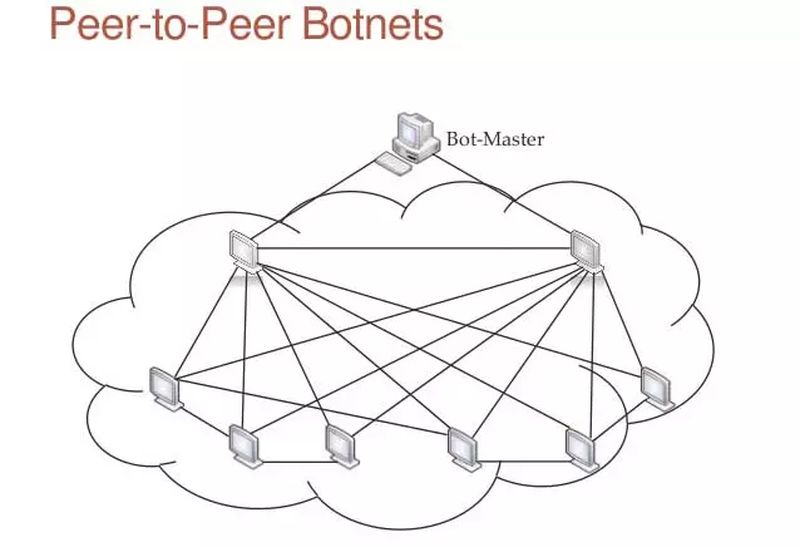
P2P botnets
Precisely the advantage of Peer 2 Peer protocols is, at the same time, their greatest vulnerability. The P2P model directly connects all computers on a network, all to all. Thus, a hacker can send the code with the commands in the form of malware to all the computers in the P2P network.
Domains
One of the easiest ways to host the code or software to infect devices is through the creation of a domain. Using hosting providers that specialize in offering high-security ratings that are difficult to penetrate, hackers host the application or code with the necessary commands. From there, they try to attract users through deceptive techniques to access the domain created by the botnet manager and thus infect massively.
How to detect that you are infected?
It is not easy for the average user to detect that their computer has been infected by a botnet. However, there are some easily visible symptoms that can help us. The first thing to bear in mind is that if we have been attacked by a botnet, it has taken control of our computer.
Unexpected errors and slowness
If we see that the operating system performs strange actions, executes commands that we have not ordered, or displays unusual error messages, we should be suspicious. Another sign that could indicate that a third party is using our computer is that it is slowing down or that the fan is running when you are not performing any process.
Exorbitant electricity bill
You finish working on your computer and turn it off. You go to sleep and turn off your smartphone to leave it charging. You might think your devices are out of harm’s way, but they’re not. The Bot Master may have entered the command to turn on the device and put it to work for him. How can we detect this? For example with a particularly high electricity supply bill.
How to protect yourself from a botnet?
Antivirus and Firewall
The main way to protect our computers is to install a good antivirus and a firewall. The former will scan your system for Trojans, malware, and any other virus variant. The Firewall will control and prohibit all access to your computer through the network.
Geographical dispersion
The dispersion in the connections to the servers to access the Internet slows down the action of botnets as it makes it difficult to filter the devices targeted by the attack. It is not a definitive solution, nor is it very effective, but it helps to contain and minimize attacks.
Pattern filtering
Different administrations are working on security to fight botnets. The US government has recently developed BotHunter, an application dedicated to analyzing network traffic and finding patterns of behavior typical of botnets.
Updates
Many of the programs we use regularly have security vulnerabilities. Usually minor, but not always. For this reason, developers often release updates and new versions that solve these problems. That is why it is important to always update applications to the latest version available.

Active prevention
Being suspicious and using common sense is, in many cases, the best strategy to prevent attacks. It is very important not to execute files that come from unknown senders or that have been downloaded from untrustworthy web pages. In fact, if you suspect a file to update an application, we recommend that you go to the official website and download it from there. The same applies to phishing, before clicking on a link we can place the mouse cursor over the link itself and analyze the destination URL (usually in the bottom bar), if the domain is not exactly the original brand is better not to click.





