WPA3 now protects your WiFi network from two new types of attacks. The vulnerabilities discovered in WPA2 led the standardization bodies to set to work to create a new, secure cipher.
This is how WPA3 arrived in our routers. This standard, however, did not get off to a good start, as it also had many vulnerabilities. Gradually, these have been patched, and new protections have been introduced against two new types of attack.
There are more and more routers with WiFi 6 and WPA3 on the market, with prices already under $50. Motherboards, laptops, and cell phones launched in the last year also support both standards. The WPA3 standard is constantly being improved.
Thus, in December 2019, WPA3 received its first major update of improvements, patching evil twin attacks when using EAP-TLS, EAP-TTLS, or EAP-PEAP. In December 2020 it included other new features against several attacks that were active in the network. In total, there are four attacks that the standard now protects against, but the WiFi Alliance has only detailed two of them.
Operating Channel Validation (OCV)
The first is Operating Channel Validation (OCV). Attacks that take advantage of network discovery systems, which do not require validation, have been used by hackers for years. One of the attributes exploited by KRACK attacks was the Operating Channel Information (OCI), which allows the access point and the device to know the frequencies, bandwidth, and maximum power that can be used in communication. In the absence of OCI authentication, man-in-the-middle attacks can be carried out.
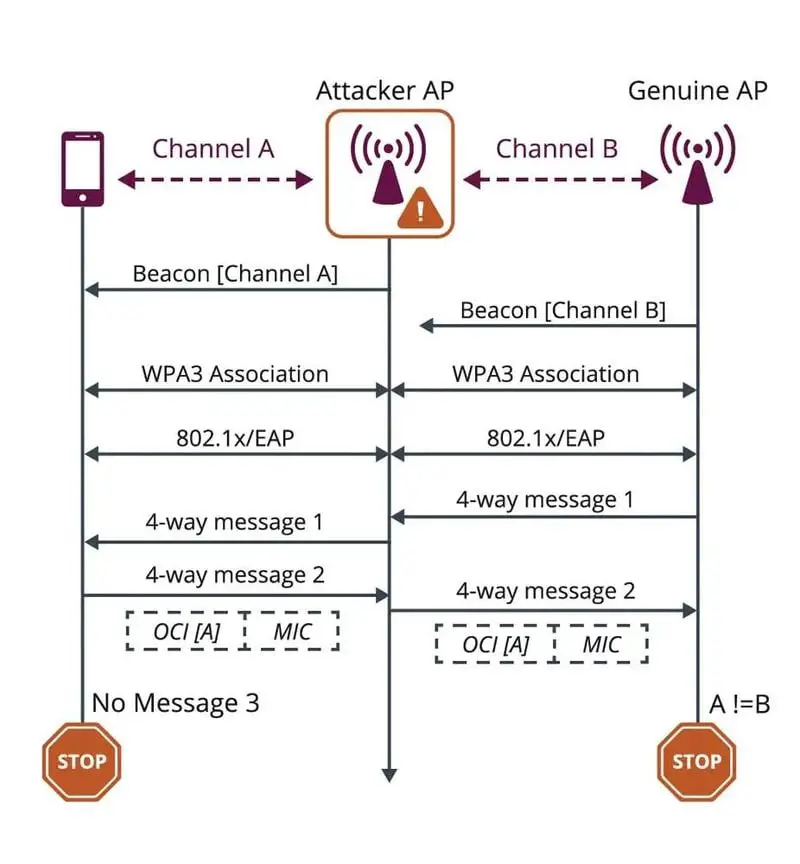
Therefore, WPA3 introduces Operating Channel Validation, which verifies the OCI to avoid any possible man-in-the-middle attack. In the image, we can see how, if the information received by the access point (the router for example) does not match the channel on which it is being received, the confirmation is aborted. Thanks to this, an attacker will not be able to position himself to carry out a man-in-the-middle attack.
Beacon Protection
The second protection feature is called Beacon Protection. With this protection measure, an access point provides its clients with a Beacon Integrity Key (BIK) during the association process and adds an integrity check message to each frame that is sent. As a result, clients associated with the access point can verify the integrity of every little piece of data that reaches them, thus preventing tamperings, such as forcing a device to use more power, reduce speed, or change channels.
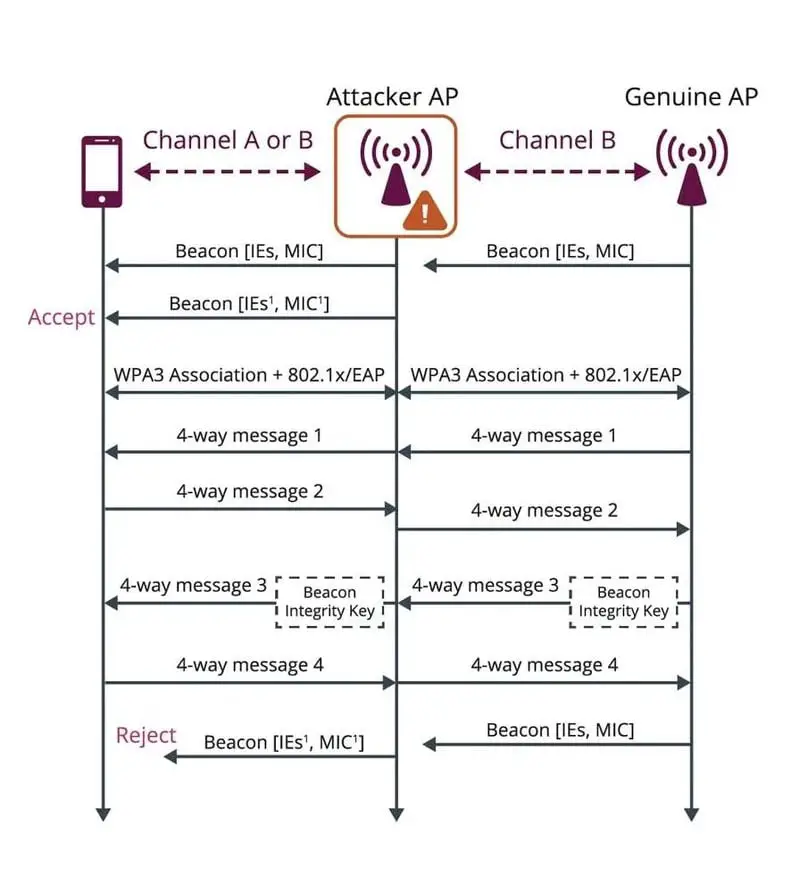
With these small improvements, the standard is gradually becoming more secure and robust, fighting against the dictionary attacks that could be carried out with WPA2, which required a complex and long password to avoid being cracked by brute force attacks. The power of today’s graphics cards, or the possibility of hiring servers for computing tasks, means that passwords of less than 10 characters can be cracked in a matter of hours or days at most with a correct dictionary if we use WPA2.





