Last week, millions of Windows machines were brought to a standstill due to a buggy update from CrowdStrike issue. The incident, which impacted around 8.5 million devices, was traced back to a bug in test software.
The faulty update slipped through the validation process, leading to widespread crashes. This CrowdStrike issue has prompted the company to commit to more rigorous testing and improved error handling for future updates.

The CrowdStrike issue has hit Microsoft outage
CrowdStrike‘s latest fiasco is not just an isolated CrowdStrike issue; it resonates with broader tech industry challenges. Microsoft also suffered an important outage because of it, which magnified the chaos to the point of affecting countries. While the roots of the Microsoft outage were different, the concurrent problems highlighted the fragile nature of cloud services and the ripple effects of software failures. Ultimately, the CrowdStrike issue was the trigger. Such incidents underscore the need for robust testing and validation processes in every domain.
What is a CrowdStrike outage?
CrowdStrike‘s Falcon software is a crucial tool for businesses and provides robust protection against malware and security breaches on millions of Windows machines. The CrowdStrike issue arose when a routine content configuration update intended to gather telemetry about potential threats instead caused a catastrophic crash. This update was part of the Rapid Response Content, a small 40KB file that did not work correctly and led to widespread system failures. This looks like old viruses. It’s like having a “Donk” sound and an endless stream of warning messages that don’t say anything and your computer shuts down involuntarily.

The anatomy of the outage
The CrowdStrike issue was linked to Rapid Response Content updating the Falcon sensor to improve malware detection. This particular update contained problematic content data that managed to pass through the Content Verifier due to a bug. CrowdStrike says it usually performs both automated and manual tests on its updates. However, Quick Response Content was not subjected to the same thorough testing as other updates, or somehow managed to pass the test, leading to the catastrophic crash.
How did it all go wrong?
The CrowdStrike issue can be traced back to a flawed assumption about the reliability of their Content Validator. In March, a new deployment of Template Types led CrowdStrike to believe their validation process was foolproof. However, this confidence proved misplaced. The problematic Rapid Response Content was loaded into the sensor’s Content Interpreter, triggering an out-of-bounds memory exception that Windows couldn’t handle, resulting in the infamous Blue Screen of Death (BSOD).
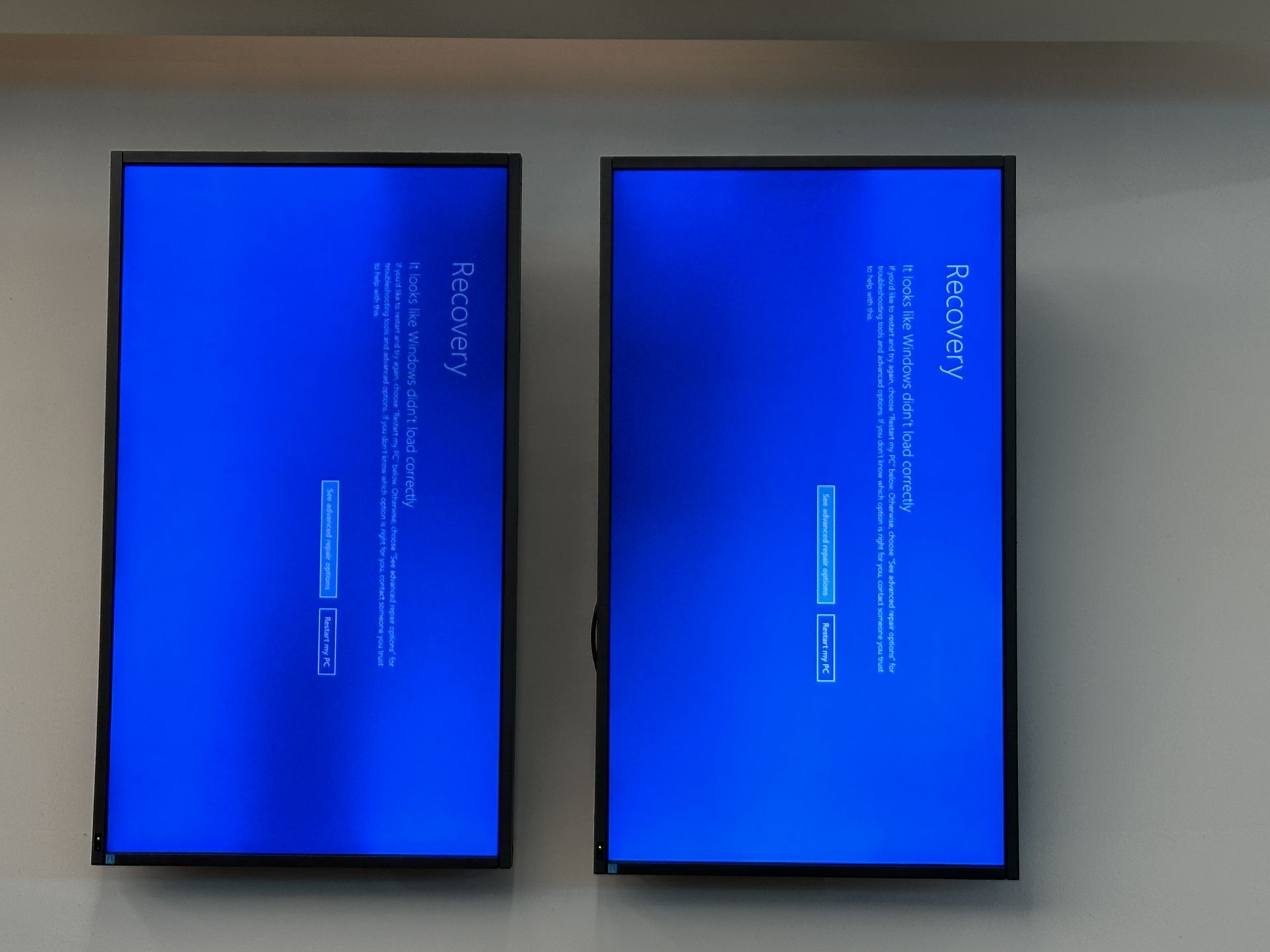
When did the CrowdStrike outage start? Timeline of the trouble
The CrowdStrike issue erupted on a Friday, a day when businesses usually wind down operations for the weekend. This timing couldn’t have been worse, as it led to immediate disruptions across numerous organizations. The faulty update, meant to enhance security, instead crippled systems, causing significant downtime and frustration.
Initial response and damage control
CrowdStrike quickly identified the problematic Rapid Response Content file as the source of the issue. Despite the quick identification, the damage was already done. Businesses relying on CrowdStrike Falcon were left scrambling to mitigate the impact of the crash. The urgency of the situation prompted CrowdStrike to publish a detailed Post Incident Review (PIR), outlining the root cause and their plan to prevent future occurrences.
Commitments to prevent future issues
In response to the CrowdStrike issue, the company has promised several measures to ensure such a disaster doesn’t repeat. These include:
- Enhanced testing: Implementing local developer testing, content update and rollback testing, stress testing, fuzzing, and fault injection.
- Improved error handling: Enhancing the error handling capabilities of the Content Interpreter within the Falcon sensor.
- Staggered deployment: Gradually rolling out updates to larger portions of the install base instead of an immediate push.
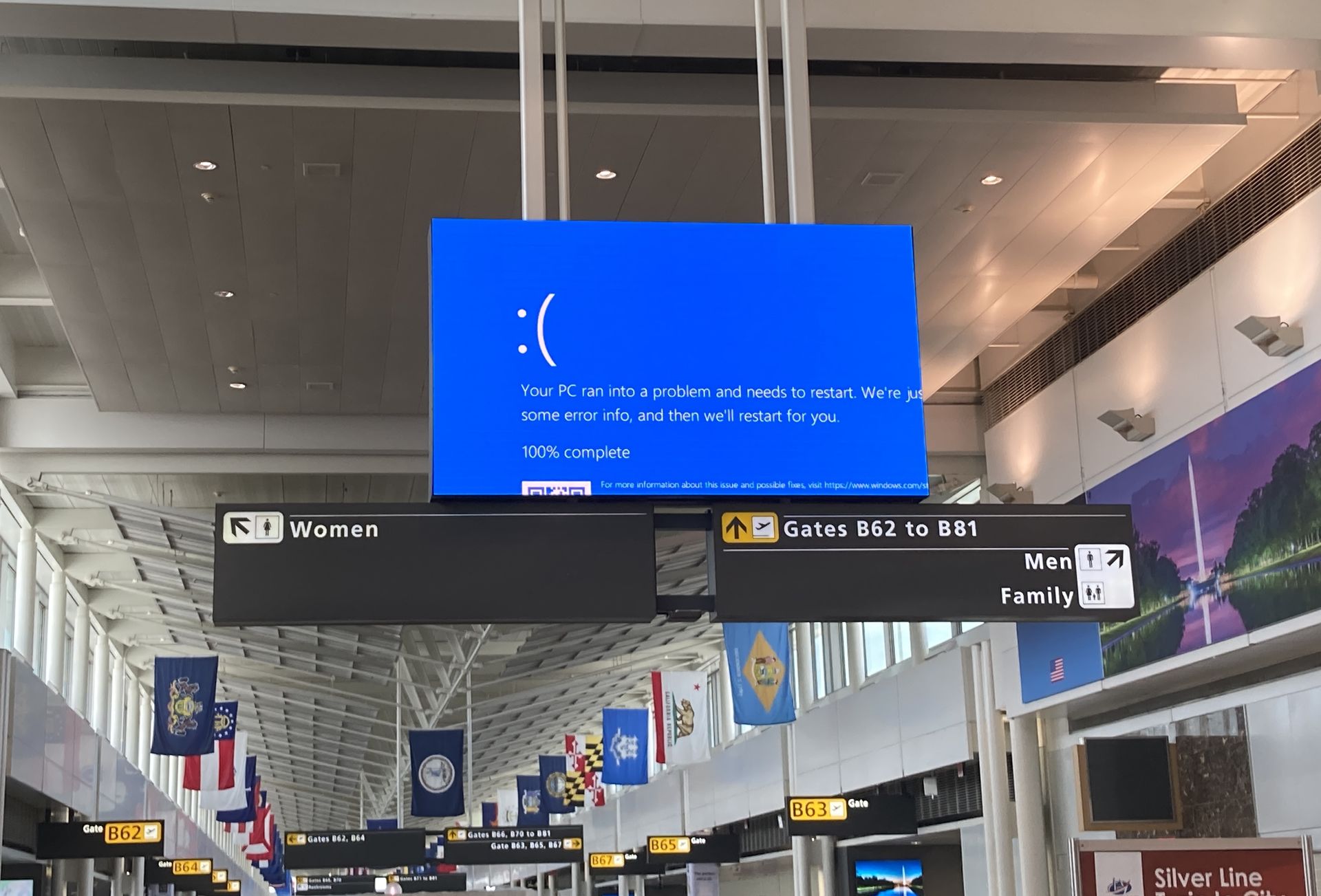
What is CrowdStrike Falcon? The protector in question
CrowdStrike Falcon is the software at the heart of this issue. It’s a cloud-based platform that provides endpoint protection, combining antivirus, threat intelligence, and endpoint detection and response (EDR). The software’s primary function is to safeguard against malware and security breaches, making it a critical tool for businesses worldwide.
How Falcon works
Falcon operates by deploying sensors at the kernel level in Windows machines. These sensors continuously monitor for suspicious activity and use AI and machine learning to enhance detection capabilities. Updates to these sensors, like the Rapid Response Content, are crucial for maintaining up-to-date protection against emerging threats.
The role of rapid response content
Rapid Response Content updates are designed to tweak the behavior of Falcon sensors, allowing them to detect new forms of malware. These updates are usually small and quick to deploy, making them an essential part of Falcon’s functionality. However, the CrowdStrike issue demonstrated the potential risks when these updates are not thoroughly validated.
The Department, and the Cybersecurity and Infrastructure Security Agency (@CISAgov) are working with CrowdStrike, Microsoft and our federal, state, local and critical infrastructure partners to fully assess and address system outages.
— Homeland Security (@DHSgov) July 19, 2024
Lessons from the CrowdStrike issue
The CrowdStrike issue serves as a stark reminder of the importance of robust testing and validation processes. While the company has outlined several measures to prevent future incidents, the tech community will undoubtedly be watching closely. Ensuring the reliability of security software is paramount, and the CrowdStrike issue has highlighted the stakes involved.
The CrowdStrike issue underscores the delicate balance between rapid updates and system stability. As businesses continue to rely heavily on such software for security, the lessons learned from this incident will be crucial in shaping future practices and protocols.
Featured image credit: Scoop News Group





