Cybersecurity has recently witnessed a new threat: A sophisticated malware targeting WordPress websites. This malware cleverly disguises itself as the popular WordFence security plugin, creating a false sense of security while disabling essential protection mechanisms and opening backdoors for attackers.
Routine check reveals a hidden WordPress malware
The discovery of this malicious software occurred during a standard investigation of a compromised WordPress website. The site administrator, initially worried about potential credit card theft, had successfully removed the immediate threat. However, a more in-depth analysis by security experts at Sucuri uncovered a more insidious problem: a malicious plugin designed to circumvent WordFence’s detection and neutralize its functions.
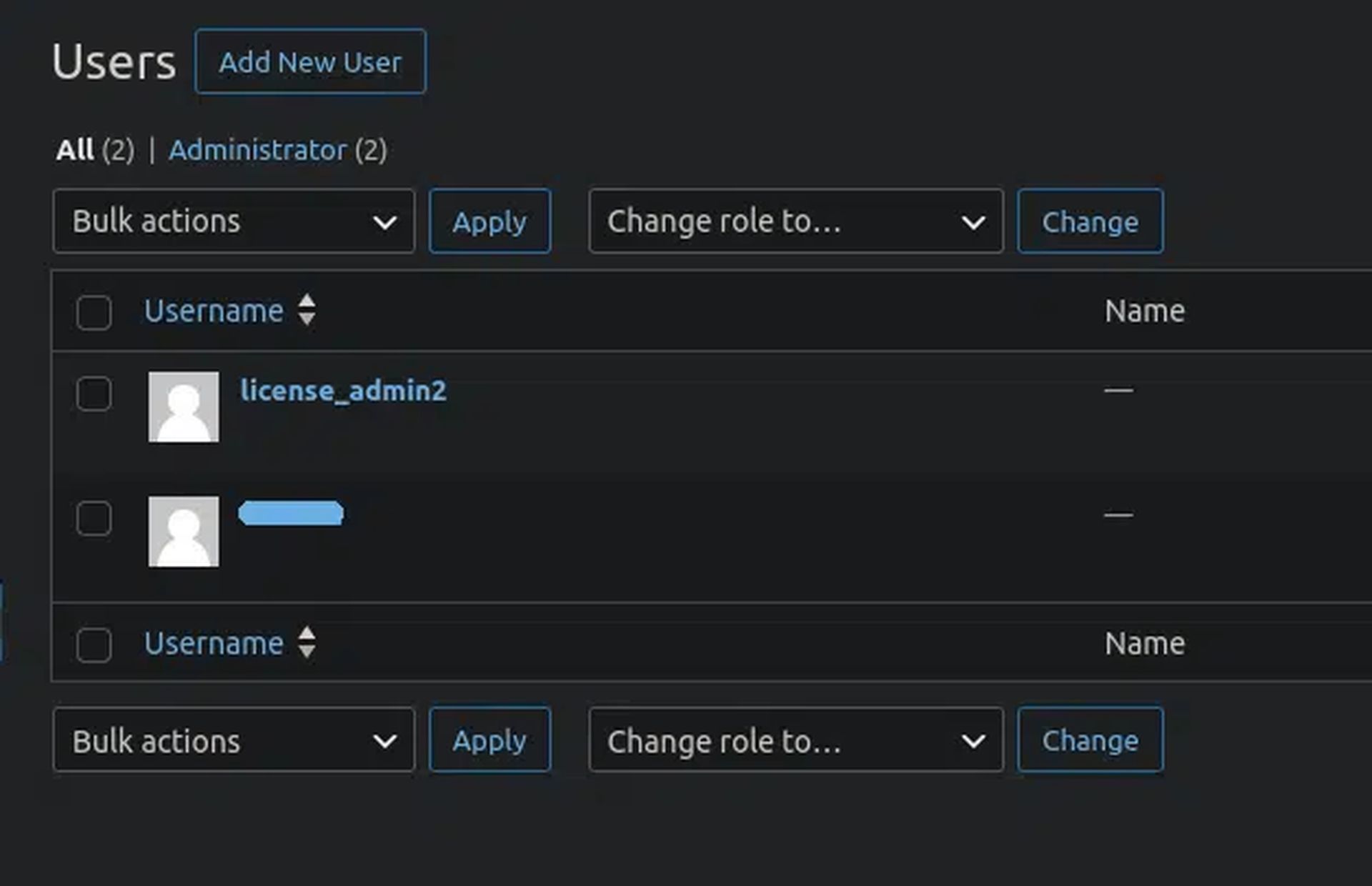
The use of malicious plugins is a common tactic employed by attackers to infiltrate WordPress websites, particularly those with compromised administrator accounts. These plugins often masquerade under generic names, blending seamlessly into the site’s environment. In this particular case, the suspicious plugin was named wp-engine-fast-action, a misleading name as the website was not hosted on WPEngine, and no legitimate plugin with that name exists.
WordFence’s vulnerability under the microscope
WordFence, boasting over 5 million active installations, is a leading security solution for WordPress websites. However, despite its robust features, including two-factor authentication and a firewall service, it is not immune to exploitation. The malicious wp-engine-fast-action plugin contained a script that concealed its true purpose using base64 encoding, concatenation, and reversed strings.
Once decoded, the plugin’s harmful intent became clear: it renamed the WordFence plugin directory to “wordfence1,” effectively disabling it, created a new malicious admin user or elevated the privileges of an existing user named license_admin2, and served as a potential reinfection vector, ensuring continued access for the attackers even after the initial malware removal.
A clever disguise
To further avoid detection, the attackers incorporated additional files (main.js and style.css) into the plugin. The main.js file contained obfuscated JavaScript code that manipulated WordFence’s settings visually, creating the illusion that security scans were active when they were not. The style.css file concealed the presence of the bogus plugin and the malicious admin user from the WordPress dashboard. This deceptive code, while short, was incredibly effective in misleading users into believing their site was secure.
How to protect your WordPress website
While WordFence remains a valuable security tool for WordPress sites, this incident highlights the importance of ensuring all its features are correctly configured and remaining vigilant for potential vulnerabilities. Sucuri recommends several measures for effective threat mitigation:
- Two-Factor Authentication (2FA): This adds an extra layer of security to logins, requiring an additional verification step beyond just a username and password.
- Securing wp-config.php: Implementing security measures such as disallow_file_edit and disallow_file_mods can prevent unauthorized modifications to this critical file.
- Regular updates: Keeping WordPress, themes, and plugins up-to-date ensures that known vulnerabilities are patched.
- Website firewall: This can protect against brute force attacks and block malicious bots.
File Integrity Monitoring: Utilizing external scanning solutions can help detect unauthorized changes to website files.
The discovery of this new WordPress malware serves as a stark reminder of the constant cat-and-mouse game between cybersecurity professionals and cybercriminals. Remember to stay informed about the latest threats and take proactive measures to protect your WordPress website.
Featured image credit: Fikret tozak/Unsplash





