The Telegram combolist leak has recently become a focal point in cybersecurity circles due to a significant data breach involving 361 million stolen accounts. These credentials, collected from a variety of sources including password-stealing malware, credential-stuffing attacks, and data breaches, have now been added to the Have I Been Pwned (HIBP) data breach notification service.
This development allows users to check if their accounts have been compromised. This blog will delve into the intricacies of Telegram combolists, the methods used to gather such vast amounts of data, and the implications of these breaches.

The mechanics of Telegram combolist
A combolist, short for “combination list,” is a compilation of usernames and passwords that have been stolen or leaked from various sources. These lists are often circulated within cybercrime communities and used for malicious activities, such as credential-stuffing attacks. In these attacks, cybercriminals use automated tools to test these stolen credentials on multiple websites, exploiting the common practice of password reuse among users.
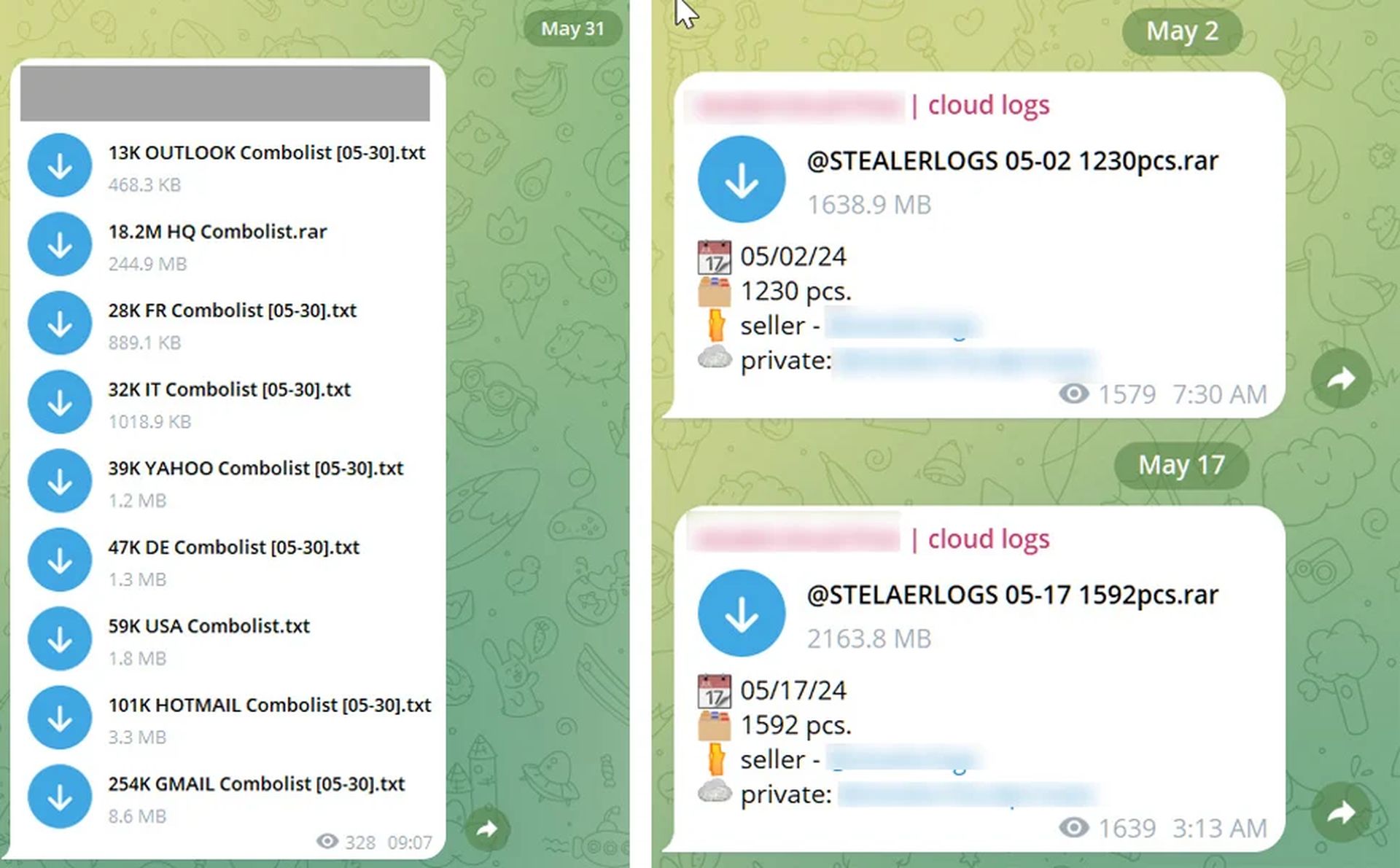
Telegram combolists are essentially large collections of stolen credentials—combinations of usernames and passwords—circulated within cybercrime communities on Telegram. Cybersecurity researchers have identified numerous Telegram channels dedicated to sharing these lists, which are used to build reputations and attract subscribers within the cybercriminal community.
Telegram has become a popular platform for cybercriminals to distribute combolists due to its encrypted messaging, large group capacities, and relative anonymity. Researchers have found numerous Telegram channels dedicated to sharing these lists, making it easy for malicious actors to access and use this data for further attacks.

The data in these combolists come from various sources:
- Credential stuffing attacks: Cybercriminals use automated tools to attempt login with stolen credentials on multiple websites, banking on the probability that users often reuse passwords across different services.
- Data breaches: Large-scale hacks of websites and services result in the leakage of user credentials.
- Password-stealing malware: This type of malware infects devices and steals saved usernames and passwords, often alongside associated URLs and other browsing data.
Researchers, opting for anonymity, compiled a significant amount of this data—122 GB of credentials—from several Telegram channels and shared it with Troy Hunt, the founder of HIBP. Hunt confirmed that this dataset includes 361 million unique email addresses, with 151 million of them previously unseen by the HIBP service.
Analysis of the massive data breach
The Telegram combolist breach has reached an unprecedented scale with the exposure of more than 361 million unique email addresses. This trove of information is not only vast but also highly granular and often includes not only email and password combinations but also URLs related to these credentials. Such data is often stolen through sophisticated means such as password-stealing malware.
Password-stealing malware infiltrates devices and extracts sensitive information, including:
- Usernames and passwords
- Cookies: Data that can be used to hijack sessions.
- URLs: Websites associated with the stolen credentials.
The data circulating through Telegram combolists is then compiled into logs and shared or sold on cybercrime markets. Given the anonymity of the researchers sharing this data, it is clear that verifying the legitimacy of each credential is an enormous task. However, Hunt verified many of the leaked email addresses using password reset forms and verified their association with the websites listed.
No site is left untouched
The size of the data set means that almost any site that allows logins can be affected. From large corporations to small forums, the reach of these credentials is vast. Even BleepingComputer, a site dedicated to cybersecurity, was involved in this data breach. Credentials associated with BleepingComputer forums were stolen through information-stealing malware, underscoring the widespread threat posed by this type of malware.
Information-stealing malware operates by infiltrating a device, capturing sensitive information, and transmitting it back to the attackers. This type of malware is commonly distributed through:
- Social media: Links or attachments in messages that lead to malware downloads.
- Cracked software: Pirated software is often bundled with malware.
- Fake VPN products: Malicious applications posing as legitimate VPN services.
- Email campaigns: Phishing emails containing malicious attachments or links.
The affected users often face the daunting task of resetting every password stored in their browser’s password manager, as well as any other accounts using the same credentials. Since these breaches usually lack timestamps, users must assume that all credentials saved in their browser have been compromised.
Information-stealing malware has become a significant challenge in cybersecurity, facilitating a range of attacks from ransomware to data theft. High-profile breaches, such as those targeting the Costa Rican government and companies like Microsoft, CircleCi, and others, often stem from credentials stolen by this type of malware. The malware’s ability to capture a wide array of data, including browser history and cryptocurrency wallets, makes it a potent tool for cybercriminals.

The stolen data is either sold on cybercrime marketplaces or used directly to breach additional accounts. This continuous cycle of theft and exploitation creates a persistent threat environment where even users who diligently change their passwords may find themselves repeatedly compromised.
Facing the reality of Telegram combolist and data breaches
The massive leak of 361 million accounts on Telegram combolist underscores the ruthless nature of cybercrime and the ever-present threat posed by information-stealing malware. While services like Have I Been Pwned provide important tools for users to control their exposure, the task of securing one’s digital presence remains challenging. The granular nature of leaked data, including URLs and cookies, highlights the need for robust cybersecurity practices and constant vigilance.
As cybercriminals continue to exploit vulnerabilities and share stolen data on platforms like Telegram, the importance of using strong, unique passwords, regularly updating software, and remaining cautious of potential malware sources cannot be overstated. The battle against credential theft and data breaches is ongoing, requiring both awareness and proactive measures from users worldwide.
Featured image credit: ilgmyzin / Unsplash





