In a concerning development, malicious advertisements have found their way into Microsoft’s AI-powered Bing Chat responses, directing unsuspecting users to fake download sites that distribute malware. Bing Chat, equipped with OpenAI’s cutting-edge GPT-4 engine, was unveiled by Microsoft in February 2023 as a formidable contender in the search industry, aiming to revolutionize online searches through interactive chat-based experiences.
The rise of malicious ads in Bing Chat
In an effort to monetize this innovative platform, Microsoft introduced ads into Bing Chat conversations in March. However, this seemingly innocuous decision inadvertently opened the door for cybercriminals, who have now begun to exploit the system by inserting ads that promote malware.
One unique vulnerability, discovered by Malwarebytes, lies in the human-like interaction provided by AI-powered chat tools, which can lead users to place undue trust in the information presented. This trust can tempt users to click on ads, a behavior less likely when scrolling through traditional search results. As a result, the already existing issue of malvertising in search platforms is further magnified by the introduction of AI assistants.
The labeling of these ads as “promoted results” when users hover over a link within Bing Chat conversations may prove insufficient to mitigate the risks. To illustrate this, researchers at Malwarebytes discovered that malicious ads masqueraded as download sites for the popular ‘Advanced IP Scanner’ utility, a tool previously exploited by cybercriminals.
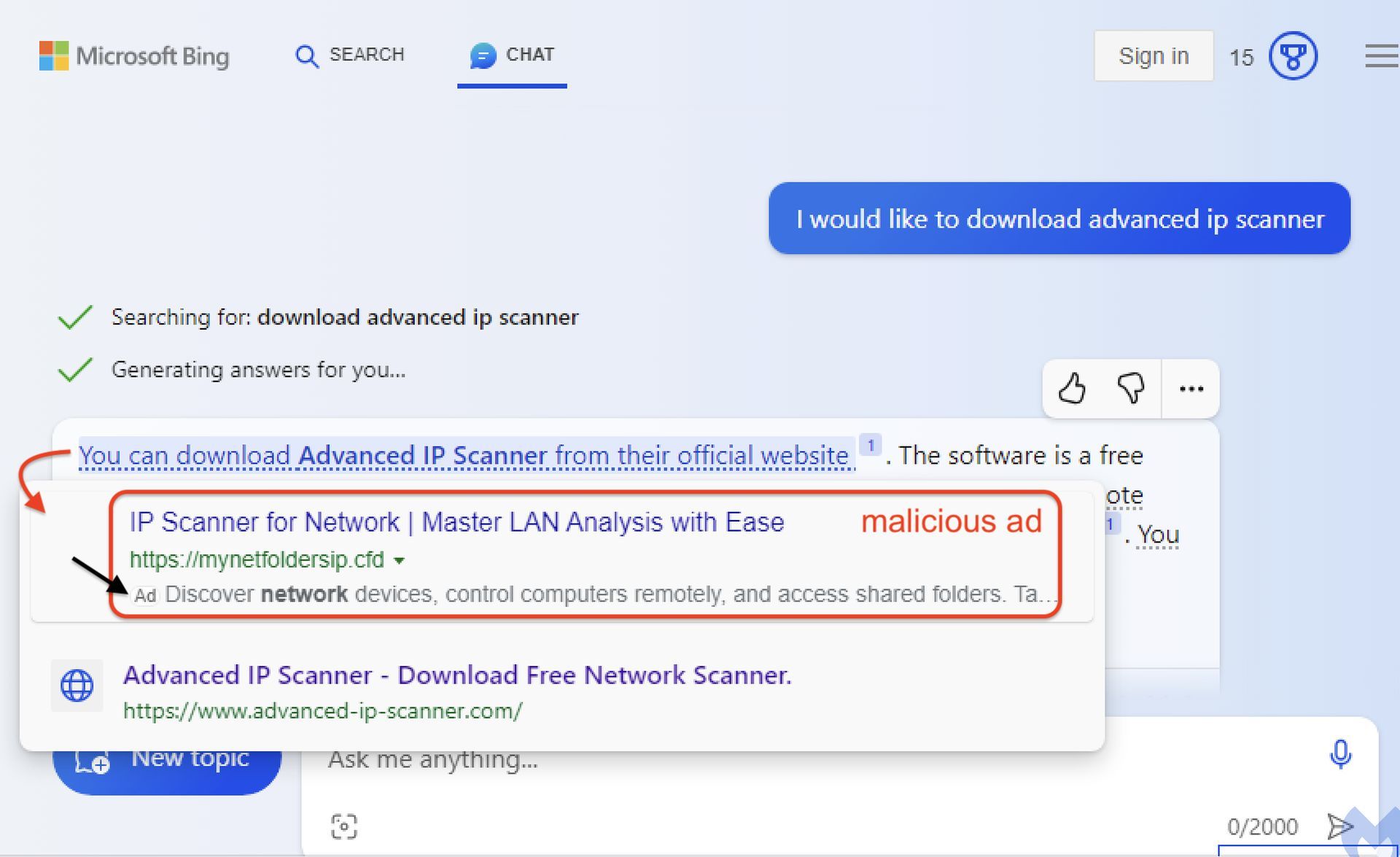
When a user inquired about downloading the Advanced IP Scanner, Bing Chat would display a link in the chat. However, hovering over the link would first show an advertisement, followed by the legitimate download link. In this instance, the sponsored link led to malvertisements pushing malware.
The intricate malvertising campaign
The malvertising campaign appeared to be the work of an individual who had compromised the advertising account of a legitimate Australian business. This campaign targeted system administrators, offering them the IP scanner, and lawyers with a lure related to MyCase law manager.
Clicking on the malicious ad for the IP scanner redirected users to a website (‘mynetfoldersip[.]cfd’), which employed various techniques to distinguish between bots, crawlers, and human victims based on IP addresses, time zones, and system indicators for sandbox or virtual machines. Subsequently, victims were redirected to ‘advenced-ip-scanner[.]com,’ a clone of Advanced IP Scanner that utilized typosquatting to deceive visitors.
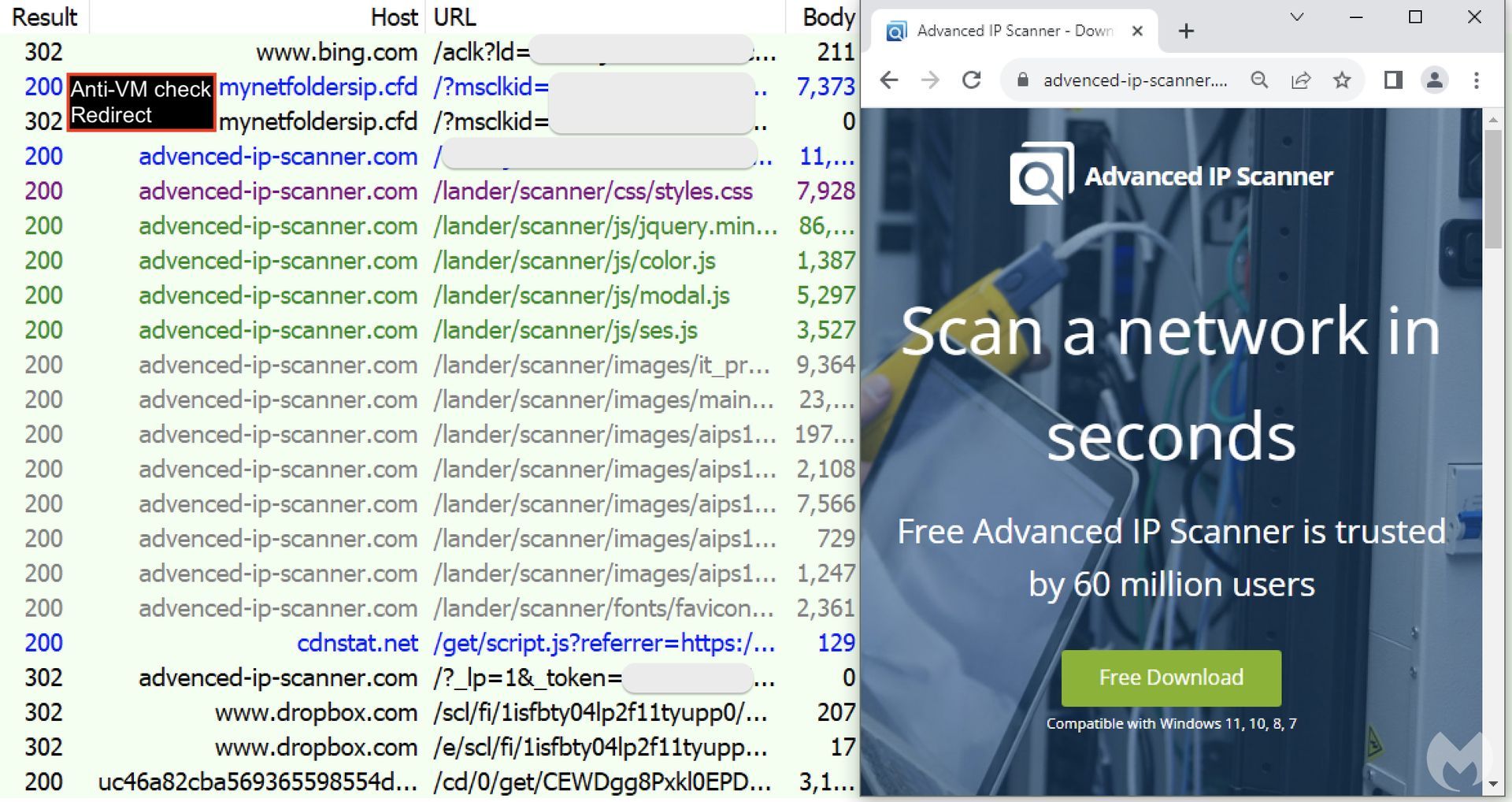
The downloaded MSI installer contained three files, one of which was a heavily obfuscated malicious script that connected to an external resource to retrieve the payload. Unfortunately, Malwarebytes was unable to identify the final payload of this malware campaign, leaving the nature of the malware it distributes uncertain. However, similar campaigns have historically distributed information-stealing malware or remote access trojans, posing severe threats to user privacy and security.
Conclusion
The infiltration of malvertising into Bing Chat conversations underscores the evolving landscape of cyber threats. It serves as a stark reminder of the importance of user vigilance when interacting with chatbot results and downloading content online. As the cyber threat landscape continues to evolve, users must remain cautious and always verify URLs before taking any action. In this age of advanced technology, staying one step ahead of malicious actors is essential to ensuring a safe online experience.





