Google has clarified that the exploited Chrome zero-day, initially thought to be within Chrome, actually resides in the libwebp library (CVE-2023-5129). This revelation comes after the CVE Numbering Authority rejected or withdrew the ID, deeming it a duplicate of CVE-2023-4863.
The latter entry has since been revised to encompass its impact on the libwebp library.

Understanding CVE-2023-5129
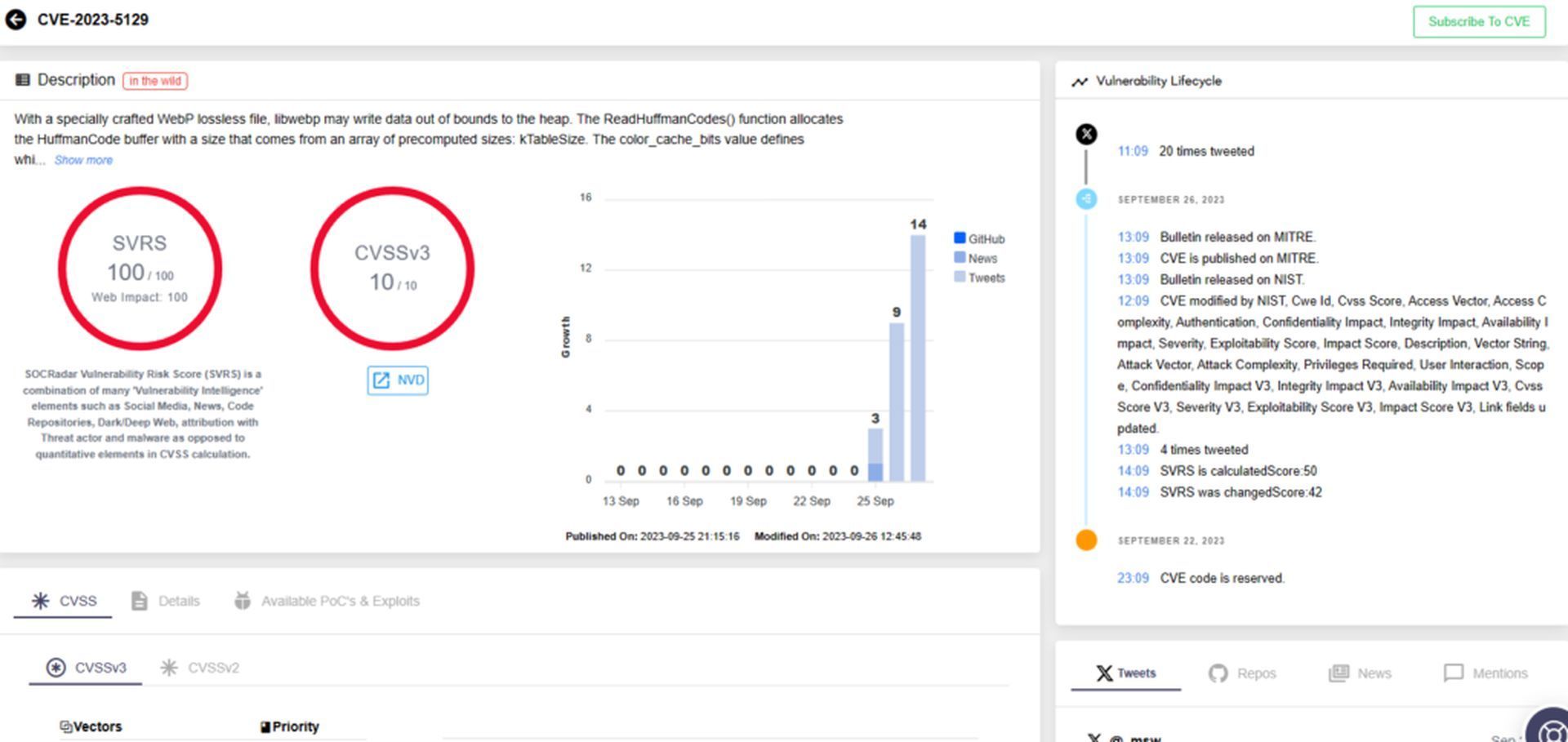
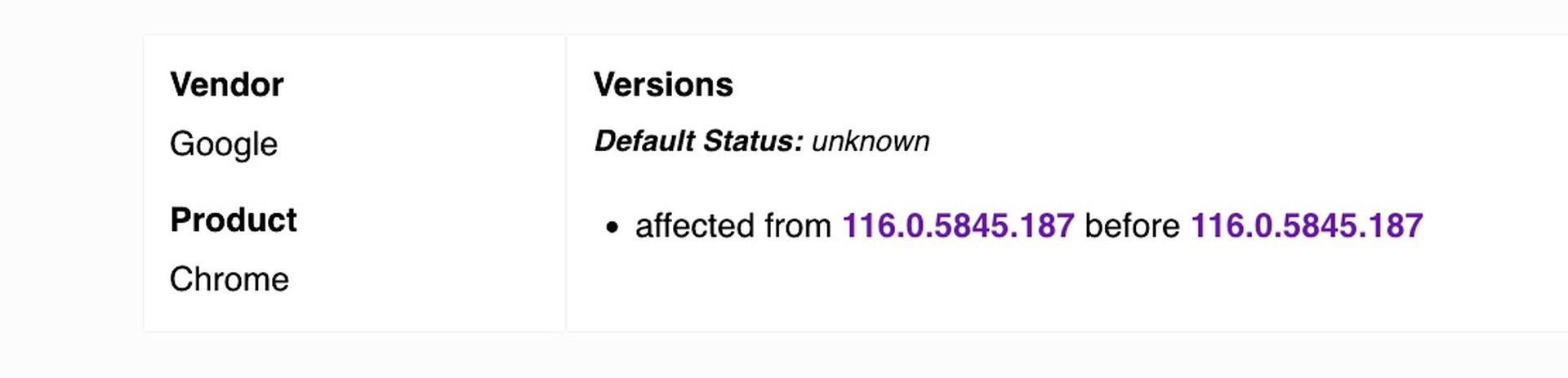
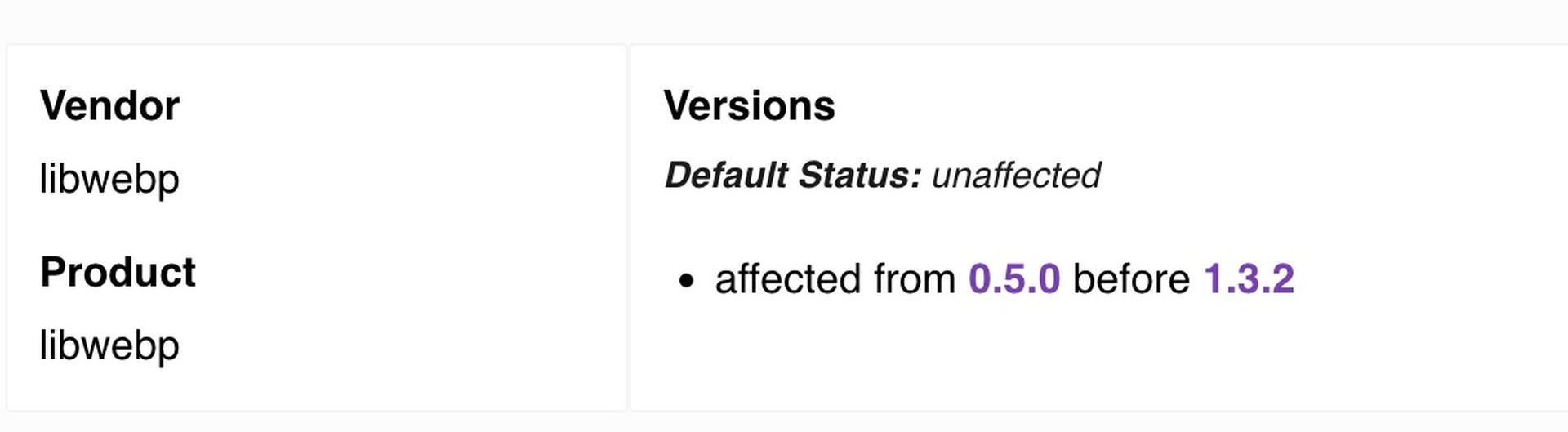
At the heart of this vulnerability lies a flawed implementation of the Huffman coding algorithm. This oversight potentially enables malicious actors to trigger a heap buffer overflow and execute arbitrary code. Notably, CVE-2023-5129 affects libwebp versions spanning from 0.5.0 to 1.3.1. However, Google has swiftly addressed this issue in version 1.3.2. Its severity is underscored by a perfect CVSS score of 10.0, signifying its critical nature.
What is the connection?
Researchers at Rezilion previously conjectured that CVE-2023-41064, a buffer overflow vulnerability within Apple’s ImageI/O framework, and CVE-2023-4863, the aforementioned Chrome zero-day, were essentially manifestations of the same flaw. As it turns out, their hypothesis was correct, leading to the emergence of CVE-2023-5129.
Widespread impact
The significance of this revelation extends across a wide spectrum of applications and platforms. The libwebp library is integral to:
- Popular container images, collectively downloaded and deployed billions of times (e.g., drupal, ngnix, perl, python, ruby, rust, wordpress).
- Various utilities dependent on libwebp.
- Leading web browsers like Chrome, Firefox, Microsoft Edge, Opera, and others.
- Numerous Linux distributions including Debian, Ubuntu, Alpine, Gentoo, SUSE, and more.
- The Electron framework, serving as the foundation for numerous cross-platform desktop applications.
- A host of other applications, ranging from Microsoft Teams and Slack to Discord, LibreOffice, 1Password, Telegram, Signal Desktop, and more.
While some have already integrated patches to address the vulnerability, others are yet to follow suit. It is imperative for consumers to heed the age-old advice: keep your operating system(s) and software updated regularly.
Empowering enterprises
For enterprises utilizing vulnerability scanners, this development signifies a significant stride forward. They can now automatically detect and remediate the vulnerability across their systems.
Taking action
Experts emphasize the urgency of swift action. Enterprises relying on vulnerability scanners now have a critical advantage in swiftly detecting and mitigating the CVE-2023-5129 threat. Tom Sellers offers a practical command for macOS users to identify patched Electron versions, fortifying their applications against potential risks.
Tom Sellers, Principal Research Engineer at runZero, has shared a shell command for macOS users to discern which of their applications are based on specific Electron versions. Versions 22.3.24, 24.8.3, 25.8.1, 26.2.1, and 27.0.0-beta.2 have received the necessary patch, providing an additional layer of security for users.
In conclusion, the identification of CVE-2023-5129 in libwebp sheds light on the interconnectedness of vulnerabilities within widely used applications and libraries. Proactive measures, including regular updates and vulnerability scans, are crucial in safeguarding systems and data from potential threats.
Meanwhile, the news of the development comes on the heels of Google’s 25th birthday. If you’ve missed it, make sure to check out our article on how Google’s 25th birthday surprise spinner marked its quarter-century celebration.
Featured image credit: Pixabay





