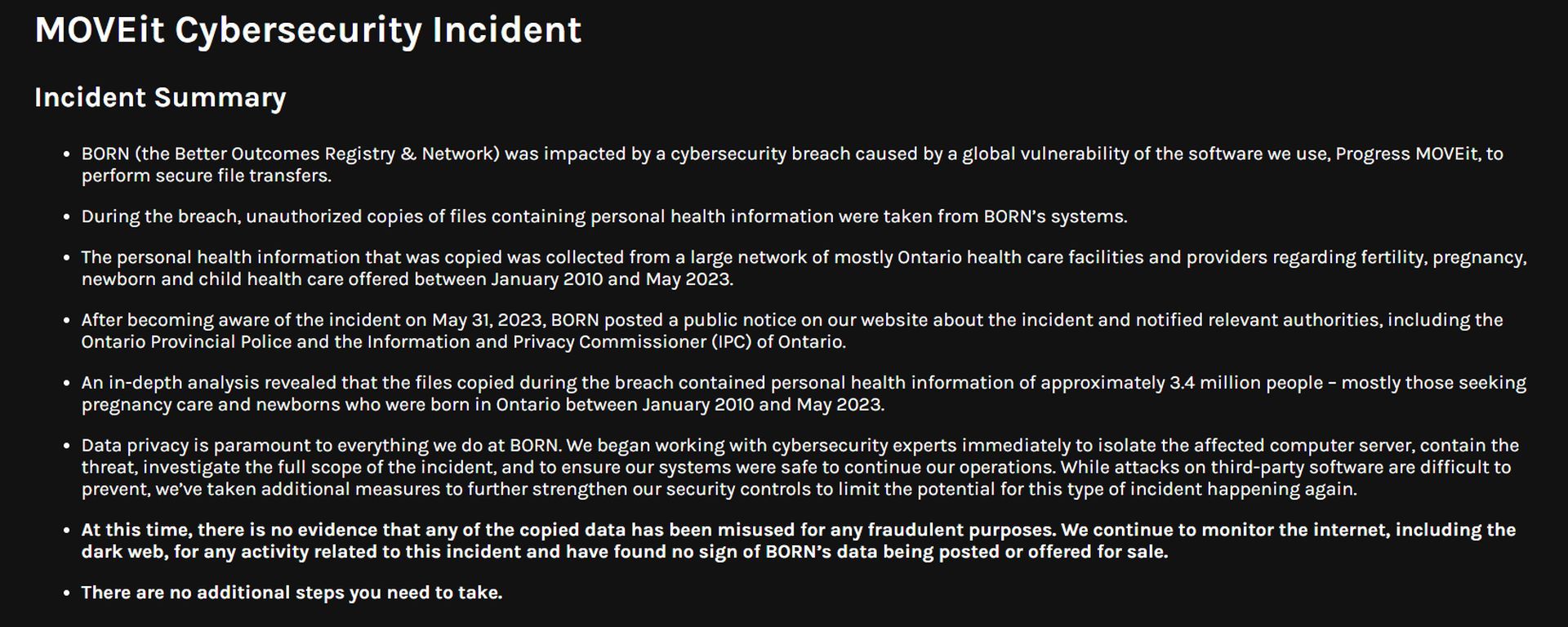
In a shocking revelation, the Better Outcomes Registry & Network (BORN) recently disclosed the major Ontario Pregnancy data breach that compromised the personal health information of approximately 3.4 million individuals, primarily mothers seeking pregnancy care and newborns born in Ontario.
This breach, which occurred in May, has raised significant concerns among Canadian security experts, who assert that it could have been entirely averted with the implementation of more robust protective measures.
The shocking revelation of the Ontario Pregnancy data breach
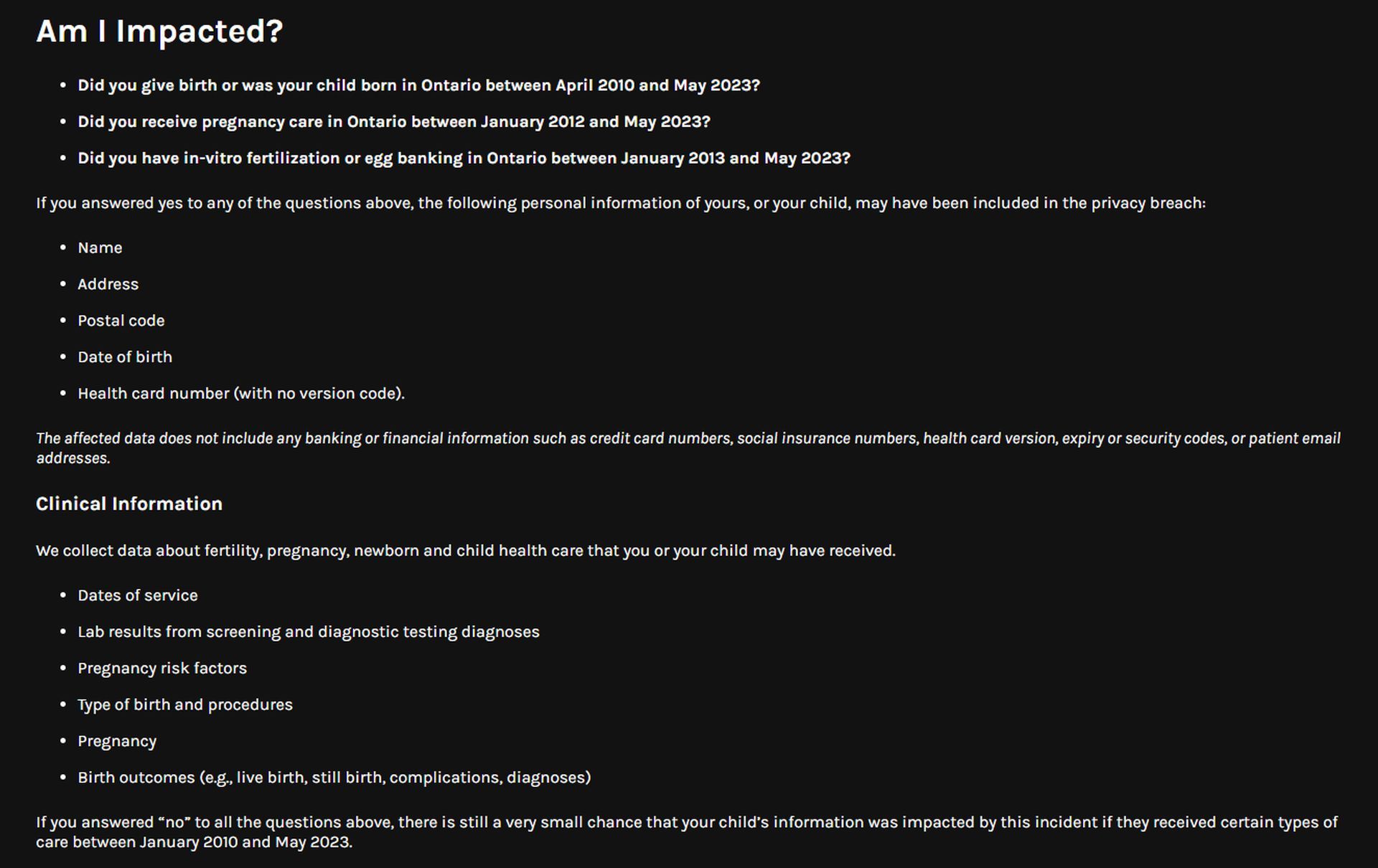
Ann Cavoukian, Ontario’s former information and privacy commissioner, expressed her dismay, stating, “This is appalling.” The compromised data, sourced from a vast network of healthcare facilities in Ontario, included sensitive information like names, addresses, dates of birth, health card numbers, lab results, and more. Cavoukian emphasized that had BORN de-identified the data by removing personal details, it would have provided the utmost protection in the event of a breach.
The missing piece of e-identification
Regrettably, BORN did not confirm the de-identification of the data, leaving a critical security gap. De-identifying information by removing personal identifiers such as names, health care numbers, and addresses is considered a fundamental step in safeguarding sensitive data. As Cavoukian pointed out, “They didn’t say that they de-identified the data and that’s the very least they should have done.”
The Ontario Pregnancy data breach in detail
BORN, an agency funded by the province, is responsible for gathering data related to pregnancies and births within Ontario. The breach, which transpired on May 31, 2023, exposed data pertaining to 1.4 million individuals seeking pregnancy care and 1.9 million infants born in the province. The cybercriminals gained access to fertility, pregnancy, newborn, and child health care records stored on a server between January 2010 and May 2023.
The aftermath and response
Upon discovering the breach, BORN promptly posted a public notice on its website and alerted the Ontario Provincial Police (OPP) and the Information and Privacy Commissioner of Ontario (IPC). However, concerns have been raised regarding the delay in notifying the public about the breach. Cavoukian expressed her concern, stating, “I’m shocked… in May they apparently contacted the OPP and the Information Commissioner of Ontario, and we heard squat from them.”
Brett Callow, a threat analyst with cybersecurity company Emsisoft, highlighted a crucial aspect of this breach: it’s not confined to Ontario alone. Given the span of the stolen data, some individuals who were in Ontario at the time may have since relocated elsewhere, emphasizing the need for vigilance. Callow cautioned, “People should be aware that their data may be out there that could potentially be misused.”
Preventing future breaches
The Ontario Pregnancy data breach was attributed to a vulnerability in the file transfer software MOVEit, developed by Massachusetts-based company Progress Software. MOVEit is employed by organizations for secure file transfers, and in this instance, it was exploited by hackers to copy files from one of BORN’s servers. This incident underscores the critical importance of regular software audits and updates to mitigate such vulnerabilities.

The Ontario Pregnancy data breach serves as a stark reminder of the critical importance of robust cybersecurity measures, particularly in handling sensitive health information. The incident underscores the necessity for rigorous de-identification practices and heightened vigilance in the face of evolving cyber threats.
While the aftermath of this breach continues to unfold, it is imperative that organizations and authorities work collaboratively to strengthen security protocols and prevent future incidents of this magnitude. In an era where data is more valuable than ever, safeguarding it must be paramount.
Meanwhile, if you are surprised by the Ontario Pregnancy data breach, you might be amazed if you were to check out how many hackings and breaches occurred only in this last week. If you wish to keep on track, make sure to refer to our articles on how the Ransomware group claims they breached Sony’s systems and the Mixin hack, 2023’s biggest crypto heist.