Google is working on improving its security measures, and with Pixel Binary Transparency, more are on the way. But what is Pixel Binary Transparency? Today, we will answer all of your questions!
Google has taken a significant stride with the introduction of Pixel Binary Transparency—an ingenious security feature tailored exclusively for its Pixel range of smartphones. This groundbreaking innovation is poised to fortify the defenses of Pixel handset users against potential cyber threats and unauthorized software manipulations. In an era where smartphones hold the keys to our personal and sensitive data, bolstering device security has become more critical than ever before.

What is Pixel Binary Transparency?
So, what is Pixel Binary Transparency? Pixel Binary Transparency stands as a beacon of security innovation, meticulously crafted by Google to elevate the security and reliability of Pixel devices, particularly smartphones. At its core, this feature revolves around guaranteeing the authenticity and untampered nature of a device’s software.
The underpinning mechanism involves a public cryptographic log that meticulously logs metadata related to official factory images. With Pixel Binary Transparency, users are empowered to mathematically validate the presence of factory images on their Pixel devices that perfectly mirror Google’s official releases. This ingenious transparency log holds a treasure trove of information about these factory images, giving users the autonomy to affirm the legitimacy of their devices independently.
The crux of this technology is rooted in its ability to bolster security by offering ironclad proof that the software on a Pixel device remains unblemished by malicious tampering or compromise.

How does Pixel Binary Transparency work?
Now that we answered your question, “What is Pixel Binary Transparency?” let’s move on to how it works. Pixel Binary Transparency functions as a multi-layered fortress, commencing its journey from the hardware of the Google Tensor system-on-a-chip (SoC), then stretching its protective wings across the Android operating system and all the way to the formidable data center.
This end-to-end fortification sets an unprecedented benchmark in mobile security, catapulting Pixel phones to the forefront of secure devices.
A defining aspect of Pixel Binary Transparency lies in its user-centric design, allowing individuals to validate the sanctity of their devices personally. This equips users with the capacity to independently ascertain if their cherished Pixel phone has undergone any malicious compromise.
Such a verification process bestows upon users a remarkable blend of transparency and control, placing them squarely at the helm of their device security.
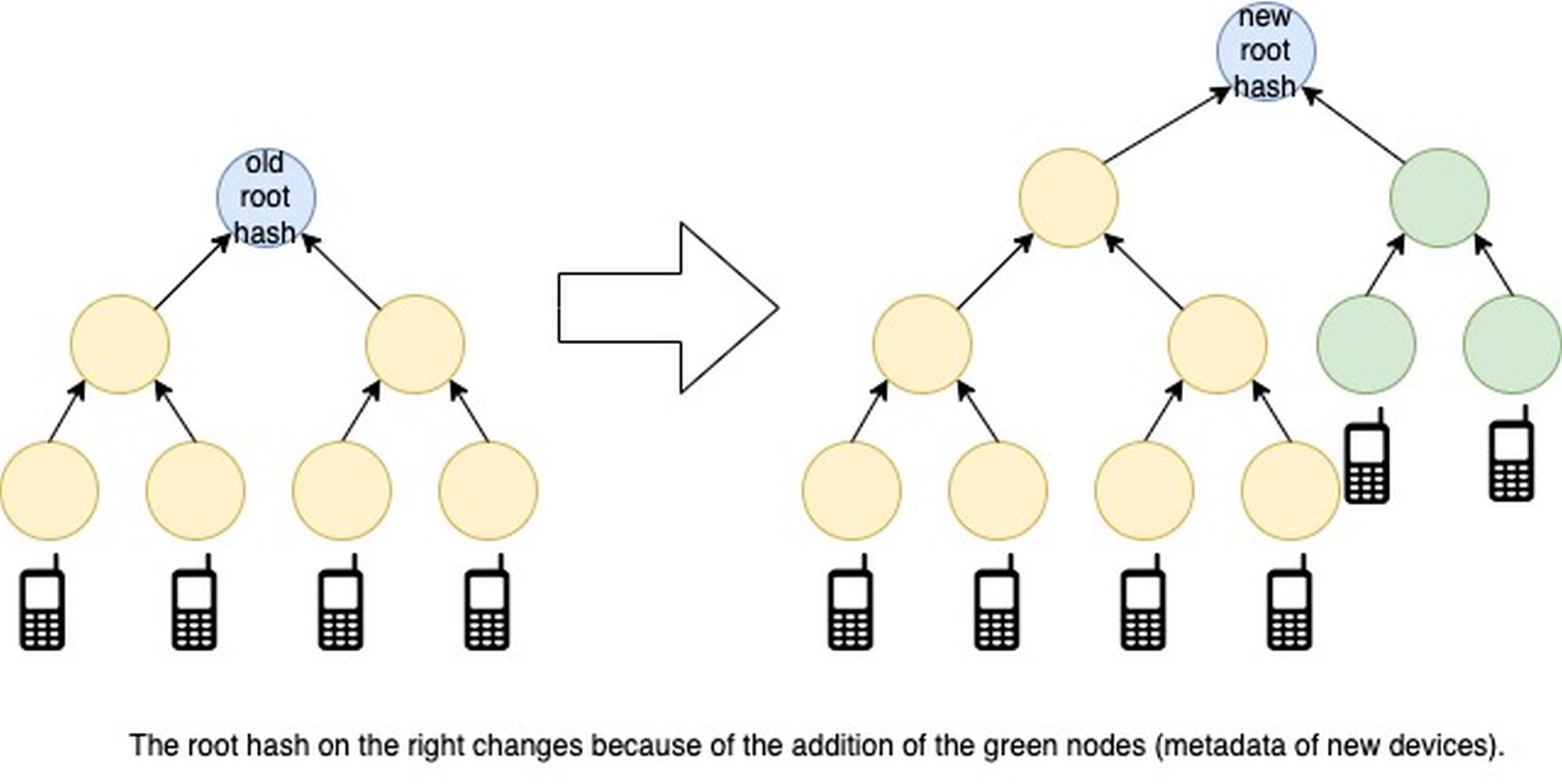
For those intrigued by the inner workings, Google sheds light on the append-only nature of the Pixel Binary Transparency log skillfully crafted through the utilization of a data structure called a Merkle tree. This structure finds its application in notable technologies like blockchain, Git, BitTorrent, and specific NoSQL databases.
Seamless Integration with Android 14
Pixel Binary Transparency seamlessly melds with Android 14, the freshest iteration of Google’s mobile operating system. This harmonious integration further solidifies the security ecosystem, creating an impervious shield against lurking threats and vulnerabilities.
Google Pixel 8 leaked: New images
The commendation from security experts for Google’s dedication to user security is both just and well-deserved. The advent of Pixel Binary Transparency demonstrates Google’s unwavering commitment to proactively tackling the evolving security landscape in the mobile domain.
By providing users with the tools to authenticate the authenticity of their devices, Google places the reins of digital security firmly in the hands of its users. This marks a technological triumph and empowers users to be guardians of their own digital domains.





