In a startling revelation, cybersecurity researchers from CYFIRMA have discovered a malicious Android app named ‘Safe Chat,’ which has been utilized by hackers to infiltrate and steal sensitive data from users of popular communication platforms like Signal and WhatsApp. Suspected to be linked to the Indian APT hacking group ‘Bahamut,’ this spyware poses a serious threat to individuals in South Asia.
In this article, we’ll shed light on the modus operandi of this sophisticated cyber-espionage campaign, while also exposing the dangers posed to unsuspecting users.

Details of the attack
The ‘Safe Chat’ app serves as the Trojan horse, inviting users under the guise of a secure chat platform. Through cunning social engineering techniques, victims are enticed into believing they are transitioning to a more secure means of communication. The app is designed with a deceptive interface, mimicking the appearance of a legitimate chat application, and even guides users through a seemingly authentic registration process, instilling a false sense of credibility.
Acquiring deep-level permissions
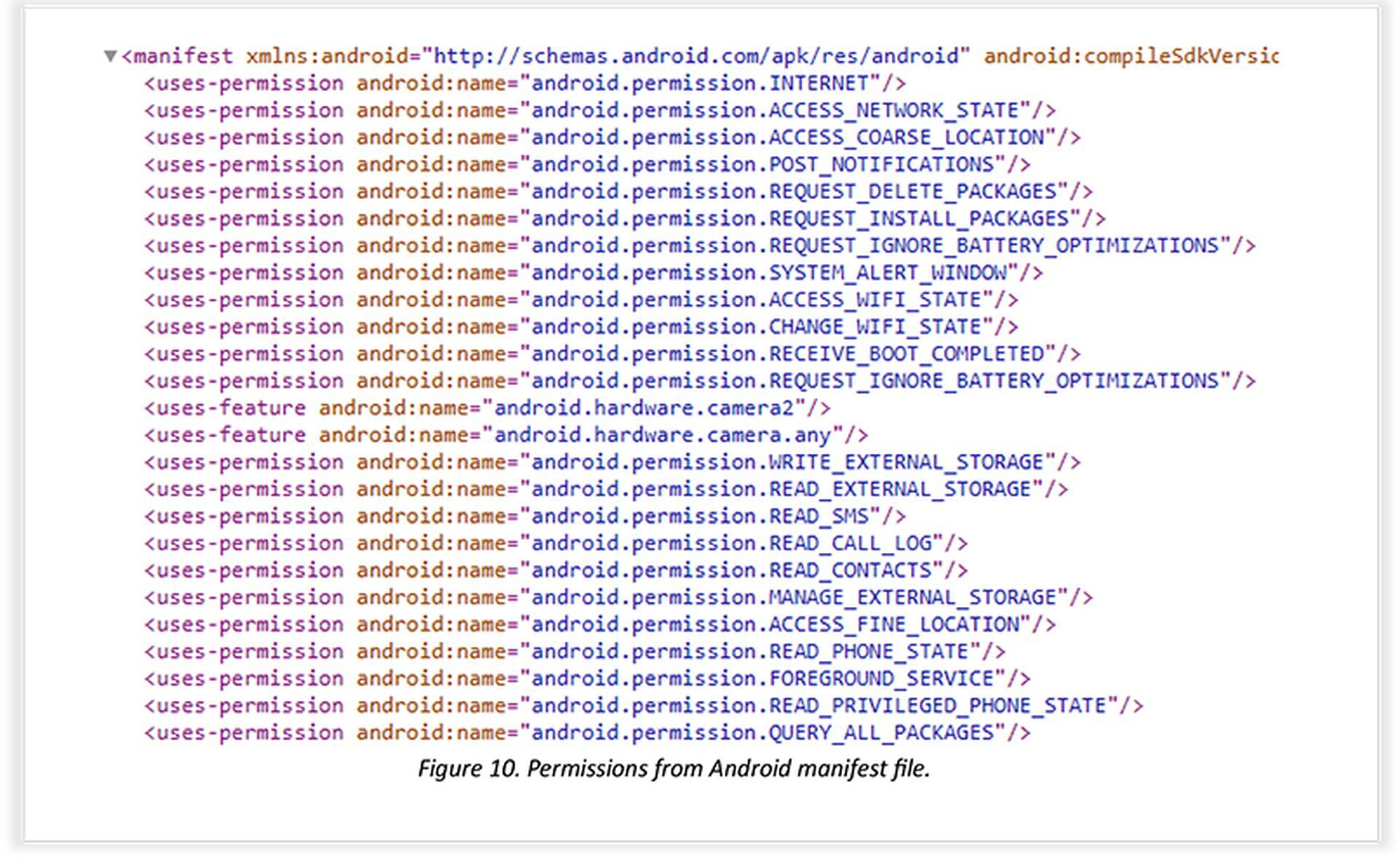
A crucial step in the attack involves obtaining permissions to utilize Accessibility Services on the victim’s device. Once acquired, these permissions are exploited to automatically grant the spyware extended access to sensitive data, including the contact list, SMS messages, call logs, external device storage, and precise GPS location information.
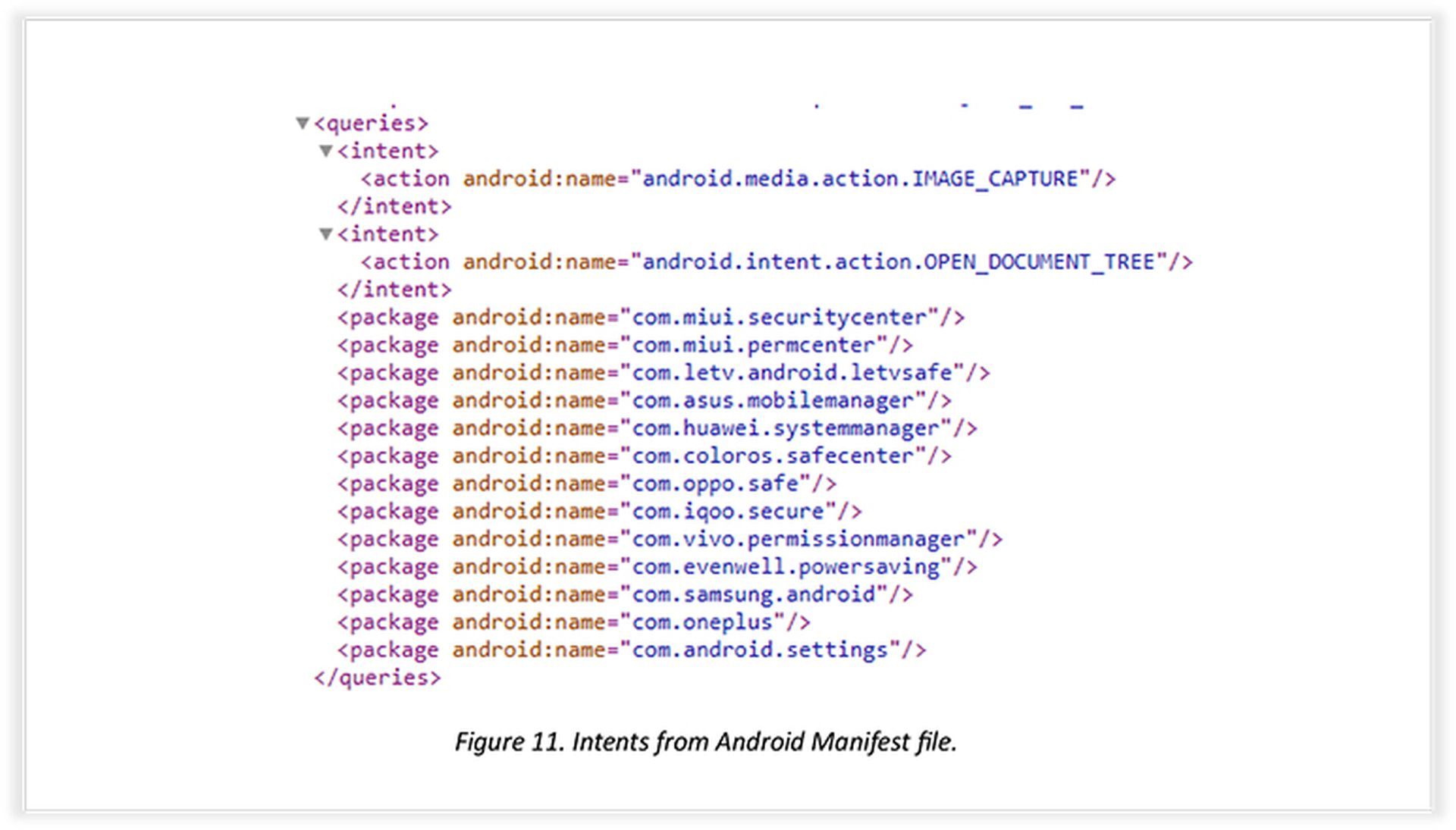
To further disguise its intentions, the malicious app interacts with other communication applications already installed on the device. By using specific intents and permissions, ‘Safe Chat’ can gain access to data from platforms like Telegram, Signal, WhatsApp, Viber, and Facebook Messenger. This strategic integration allows the spyware to remain undetected while silently pilfering information from unsuspecting users.
Data exfiltration and evasion techniques
A dedicated data exfiltration module facilitates the transfer of stolen information from the infected device to the attacker’s command and control (C2) server through port 2053. The stolen data is encrypted using sophisticated algorithms, including RSA, ECB, and OAEPPadding, which provide an added layer of security for the hackers. Furthermore, the attackers employ a “letsencrypt” certificate to circumvent interception attempts, making it exceedingly challenging for security systems to detect and halt the exfiltration process.
Bahamut: State-sponsored hacking group?
CYFIRMA’s researchers claim to have amassed compelling evidence linking the ‘Bahamut’ group to activities associated with a specific state government in India. Notably, the group shares striking similarities with the ‘DoNot APT’ (APT-C-35) threat group, also believed to be state-sponsored. The shared certificate authority, data-stealing methodologies, and targeting scope all point towards a potential collaboration or overlap between the two groups.
Last month, an international cyber attack has also been perceived as a state-sponsored one when Chinese hackers breached US government using a Microsoft cloud bug.
The emergence of ‘Safe Chat’ as a tool for data theft underscores the growing sophistication of cyber-espionage campaigns. As hackers continue to exploit social engineering tactics and advanced evasion techniques, it is imperative for users to exercise caution and only install apps from trusted sources. Vigilance and the adoption of robust cybersecurity measures are essential to safeguard personal data and prevent falling victim to such insidious attacks. Public awareness, collaboration between security researchers, and prompt action by tech companies remain vital in the ongoing battle against cyber threats.
Featured Image Credit: Joan Gamell/Unsplash





