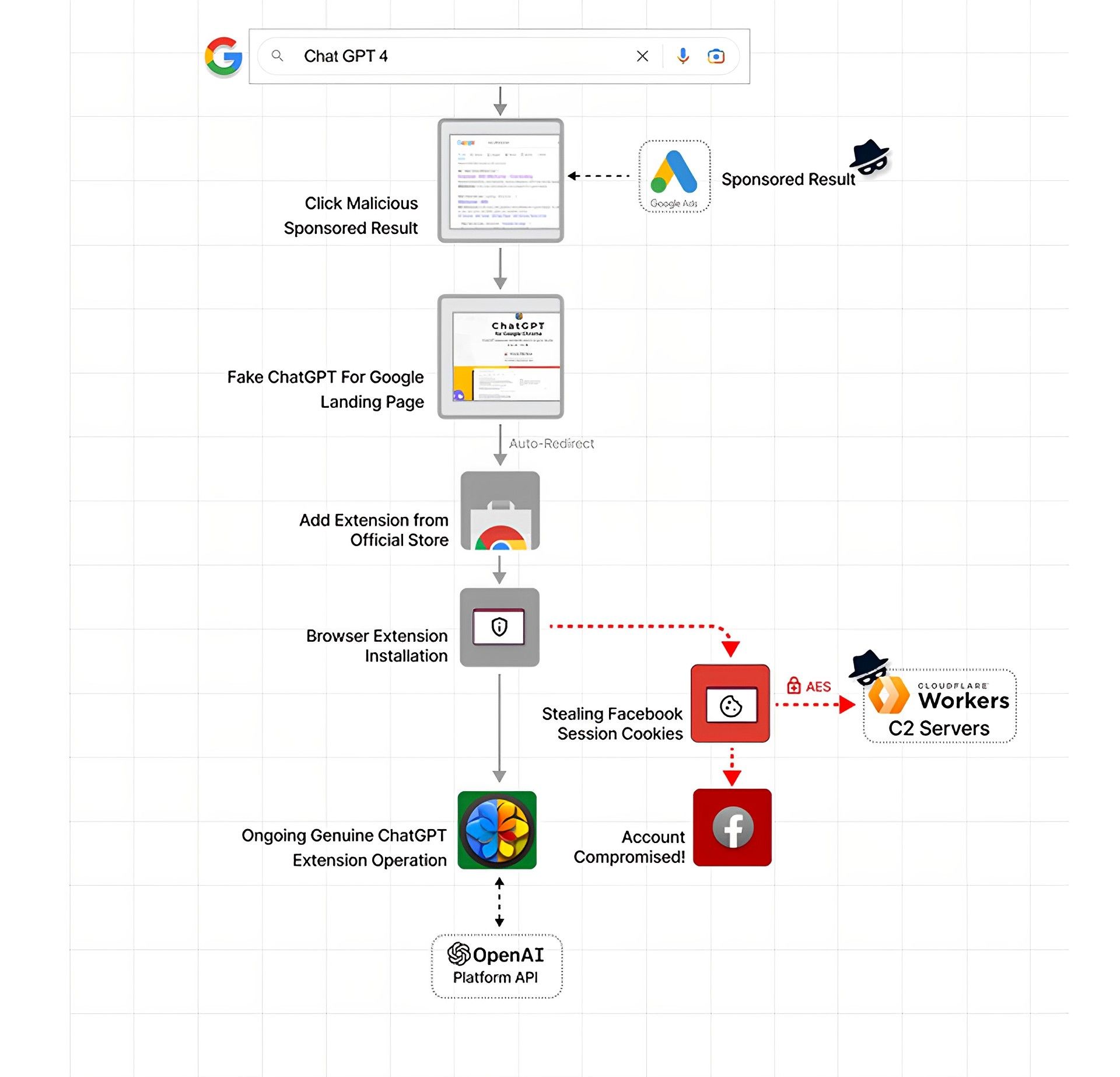
A fake ChatGPT extension on Chrome browser that used OpenAI’s ChatGPT service to gather Facebook session cookies and take over user accounts has been removed by Google from the official Web Store. Therefore take caution if the current surge in interest in AI has you extremely captivated. There are some negative items waiting to jeopardize your Facebook account in search engine results.
Prior to being removed, the “ChatGPT For Google”, the fake ChatGPT extension had amassed over 9,000 installations since March 14, 2023. It was a trojanized version of an authentic open-source browser add-on. On February 14, 2023, it was initially posted on the Chrome Web Store.
How did the fake ChatGPT extension spread?
Nati Tal, a researcher at Guardio Labs, claims that the fake ChatGPT extension spread using deceptive sponsored Google search results that were intended to lead unwary users searching for “Chat GPT-4” to phony landing pages pointing to the false add-on.
From the initial search to infection and compromise, the attack proceeds as follows:
- Google provides a sponsored ad as the result of your search for Chat GPT-4.
- The destination website asserts that it provides a Chat GPT format within your search results.
- This website eventually links you to the official extension shop where you may download a Chrome extension.
Since the extension itself isn’t what it seems to be, you might anticipate some malicious behavior at this point. For all, the majority of frauds present phony apps, games, and software, and since they are really empty shells, these programs often have no effect. The tool in this instance does incorporate Chat Talk into search results. This is due to the fact that the individuals responsible for it used a valid open-source product to make their own version of it.
Installing the extension activates the covert capability to secretly enable the ability to harvest Facebook-related cookies and exfiltrate them to a remote server in an encrypted way in addition to adding the functionality that was promised, i.e., augmenting search engines with ChatGPT.
The main objective of the game, however, is to tamper with Facebook profiles. The fake ChatGPT extension tries to steal a few cookies when it first starts up. A virus author may attempt to log in to the website for which they took the authentication cookie if they are successful in stealing it from your browser during a session.
Before delivering the stolen cookie(s) to the extension’s author’s server, the extension expressly scans for Facebook cookies. The stolen cookies are encrypted before being sent in an effort to stealthily remove them from the target system. In order to prevent specific security technologies from detecting a problem, encryption is used.
After the creators of the extension gain access to the Facebook account, they modify the name, profile picture, and login information before publishing whatever is required to advance their campaign. The researchers cite ISIS propaganda images as well as more general references to spam and phony services as examples.
It is now the second fake ChatGPT extension on Chrome to be found in the wild as a result of the development. Sent through sponsored posts on the social media site, the other extension likewise served as a Facebook account thief. With such news, the security concerns with ChatGPT seem to grow: ChatGPT Italy ban draws attention to data privacy
If anything, the data provide further evidence that cybercriminals are capable of quickly modifying their tactics in order to take advantage of ChatGPT’s popularity in order to spread malware and carry out targeted assaults.
“For threat actors, the possibilities are endless — using your profile as a bot for comments, likes, and other promotional activities, or creating pages and advertisement accounts using your reputation and identity while promoting services that are both legitimate and probably mostly not,” Tal said.





