An ongoing supply chain attack that has 3CX hacked purportedly uses a digitally signed and trojanized variant of the 3CX Voice Over Internet Protocol (VOIP) desktop client to target the company’s clients.
The 3CX Phone System is used by more than 600,000 businesses globally and has over 12 million daily users. 3CX is a VoIP IPBX software development company.
Numerous well-known businesses and institutions, including American Express, Coca-Cola, McDonald’s, BMW, Honda, Air France, Toyota, Mercedes-Benz, IKEA, and the UK’s National Health Service, are among the company’s clients (who published an alert on Thursday).
Security researchers from Sophos and CrowdStrike have reported that the attackers are aiming their attacks at 3CX softphone software users running Windows and macOS.
“The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity,” CrowdStrike’s threat intel team said.
“The most common post-exploitation activity observed to date is the spawning of an interactive command shell,” Sophos’ Managed Detection and Response service also warned.
While Sophos experts claim they “cannot validate this attribution with high confidence,” CrowdStrike believes the attack was carried out by the Labyrinth Collima hacking organization, which is supported by the North Korean government. CrowdStrike’s claim worries many 3CX users although it was not yet confirmed. Lately, such worrying hacking news have seen a spark: Linus Tech Tips hacked on YouTube
The behavior of Labyrinth Collima is known to overlap with that of other threat actors, such as Lazarus Group by Kaspersky, Covellite by Dragos, UNC4034 by Mandiant, Zinc by Microsoft, and Nickel Academy by Secureworks.
How was 3CX hacked in a supply chain attack?
In reports released last Thursday evening, SentinelOne and Sophos also disclosed that the trojanized 3CX desktop program is being downloaded as part of a supply chain attack.
SentinelOne has called this supply chain assault “SmoothOperator.” It begins when the MSI installer is downloaded from the 3CX website or an update is issued to a desktop application that has already been set up.
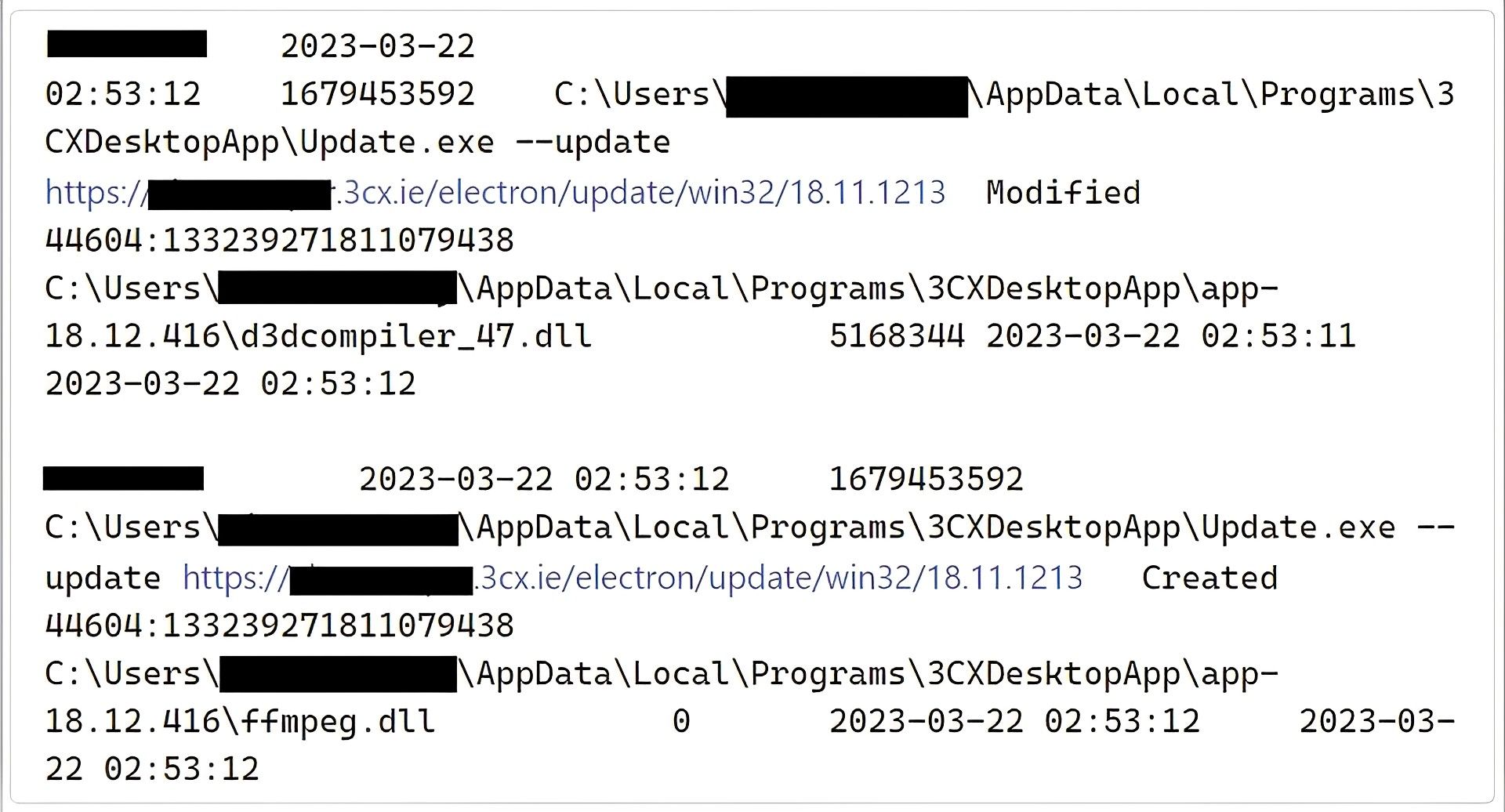
The malicious DLL files ffmpeg.dll [VirusTotal] and d3dcompiler 47.dll [VirusTotal] are extracted when the MSI or update is installed and are utilized to carry out the next phase of the attack.
Even though the malicious ffmpeg.dll DLL will be sideloaded and used to extract and decrypt an encrypted payload from d3dcompiler 47.dll, Sophos asserts that the 3CXDesktopApp.exe executable is not malicious.
In order to download icon files stored on GitHub that include Base64 encoded text appended to the end of the images, this encrypted shellcode from d3dcompiler 47.dll will be performed.
These icons are kept in a GitHub repository, which indicates that the first icon was posted on December 7th, 2022.
According to SentinelOne, the malware uses these Base64 strings to download a final payload—an unknown DLL—that steals information from the infected devices.
The user profiles for Chrome, Edge, Brave, and Firefox can contain data and credentials that this new malware is capable of stealing as well as system information.
“At this time, we cannot confirm that the Mac installer is similarly trojanized. Our ongoing investigation includes additional applications like the Chrome extension that could also be used to stage attacks,” SentinelOne said
Meanwhile, the 3CX CEO Nick Galea stated in a forum post on Thursday morning that malware had been inserted into the 3CX Desktop program. Galea advises all users to uninstall the desktop application and switch to the PWA client as a result.
“As many of you have noticed the 3CX DesktopApp has a malware in it. It affects the Windows Electron client for customers running update 7. It was reported to us yesterday night and we are working on an update to the DesktopApp which we will release in the coming hours,” Galea shared in the 3CX forums.





