Many of the businesses still carry out their communications through email. While the number of email users globally is expected to reach 4.6 billion by 2025, emails continue to be seen by cybercriminals as the most widespread attack vector for initiating attacks, ranging from the use of insecure accounts to social engineering.
Remote working turned government institutions into targets
During the tough times of 2020 caused by the pandemic, cybercriminals developed increasingly sophisticated tactics to circumvent the security measures taken by companies. They have threatened and attacked many businesses and government institutions. The most important reason for the increase in the risks related to email security last year was that cybercriminals started to target employees more in the home environment, as many companies switched to remote work during the pandemic period.
The 2021 Email Vulnerability Report prepared by Keepnet Labs, a London-based cybersecurity company, revealed that there has been an increase in phishing, malware, and ransomware attacks over email after the COVID-19 outbreak. The report also shows that these attacks could easily bypass company-owned email security tools such as anti-spam filters, firewalls, sandbox, and other border protection technologies.
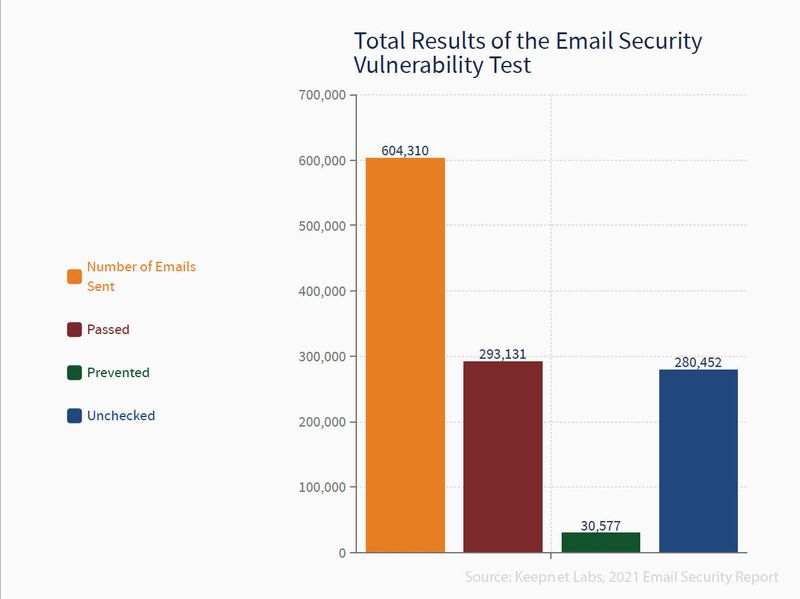
More than 90% success in reaching the inboxes
Keepnet sent 604,310 e-mails to test for email-based security vulnerabilities. While 90.56% of the emails successfully reached the target inbox, only 9.44% were blocked by the customer’s security tools. Also, 280,452 emails were not checked, which means the system was unable to detect if the malicious email had reached the inbox.
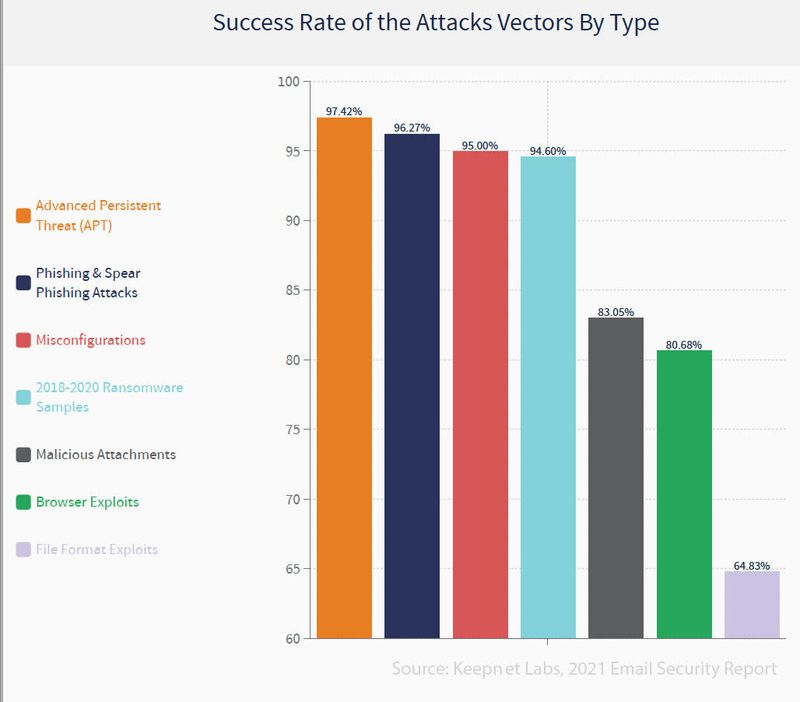
The biggest threat to email security in 2020: Advanced Persistent Threat (ATP)
When we look at the success rate of attack types in bypassing security technologies and reaching target inboxes, we see that 4 types are successful above 90% rate and all of them bypass security most of the time. These 4 attack types and their success rates are as below:
- Advanced Persistent Threat (ATP) (97.42%),
- Phishing and Spear-Phishing (96.27%)
- Security Misconfiguration (95%)
- Ransomware 2018-2020 (94.60%)
Tech ranked the most unsuccessful sector in terms of cybersecurity
The report also identified the most unsuccessful sectors in the face of email attacks. Technology, consultancy, and financial services were the three most unsuccessful sectors in defense against such attacks, while the technology sector taking the first place showed how far behind it was in using its solutions. You can see the list of the most unsuccessful sectors below:
- Technology
- Consultancy
- Financial Services
- Education
- Real estate
- Biotechnology
- Service Sector
- Holding/Conglomerates
- Pharmaceuticals
- Publishing
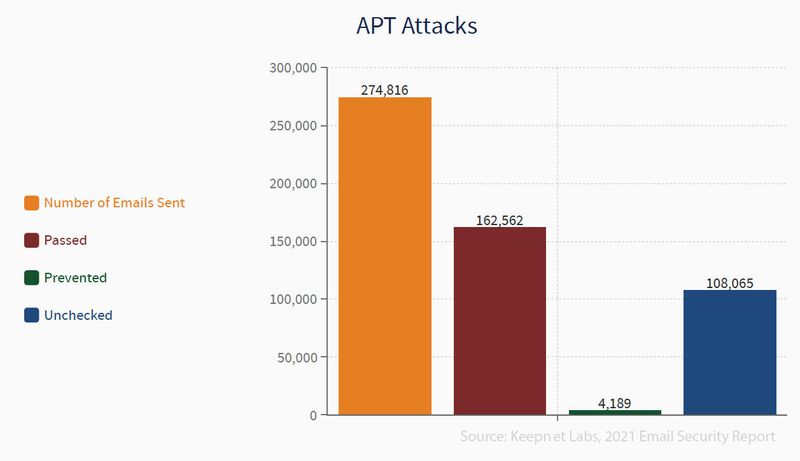
40% of the recipients did not check emails sent for ATP testing
Advanced Persistent Threats (APT), the most threatening type of attack in today’s email security, is an advanced and highly targeted type of cyberattack in which a hacker accesses a system and goes undetected.
Keepnet sent 274,816 e-mails as part of the report to test for APT-focused vulnerabilities. While 162,562 of the emails sent successfully reached the target inbox, only 4,189 were blocked by security tools. In addition,108,065 of the recipients (around 40 percent) did not check the emails in question. This suggests that ATP is more successful at bypassing security technologies and reaching target inboxes than phishing and other types of attacks.
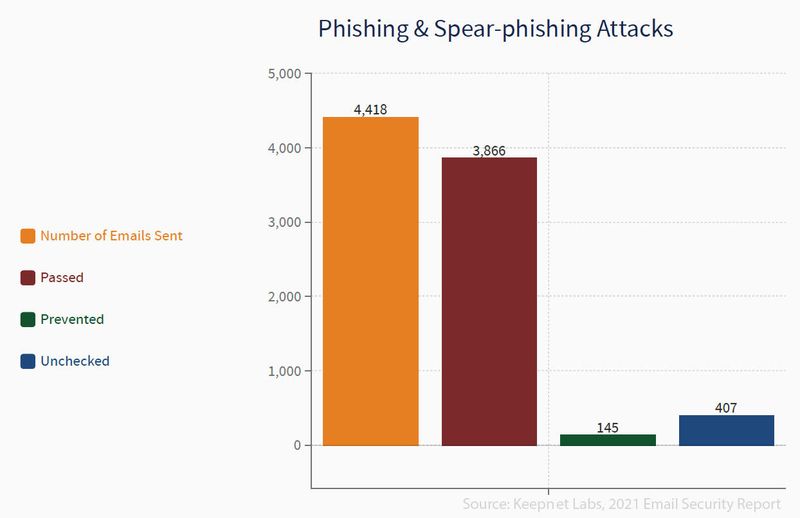
Security tools are helpless against phishing and misconfiguration attacks
Phishing stands out as another cyber attack that uses obfuscated e-mail as a weapon. In this type of attack, the goal is to trick the email recipient into believing something they want or need in the message and get them to click a link or download an attached file.
Phishing emails are sent to many recipients with the expectation that only a few recipients will respond, while spear-phishing emails target a specific person, organization, or business. Keepnet sent 4,418 emails to detect vulnerabilities in phishing and spear-phishing attacks, and 3,866 of these emails found their way to the target inboxes. Of these emails, only 145 were blocked by recipients’ security tools, while 407 were not checked by recipients.
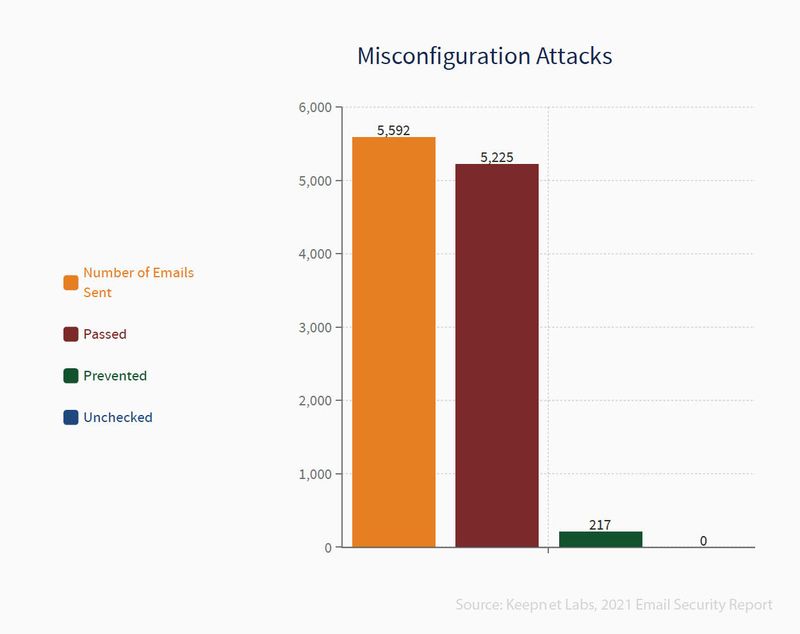
Another type of attack that causes many security vulnerabilities are Security Misconfiguration attacks. Keepnet sent 5,592 emails to test the resulting vulnerabilities, and 5,225 of them reached the target inbox. And only 217 emails were blocked by recipients’ security tools.
Ransomware attacks increase with the shift to remote working
Ransomware attacks include a type of malware that encrypts target systems or files, and the cybercriminal demands payment from the victim to recover the system or files. In the first quarter of fiscal 2020, ransomware attacks also increased significantly with the shift to remote working due to the pandemic. The main reason for this increase was the insufficient cybersecurity measures at home. Keepnet sent 106,169 emails to test for ransomware vulnerabilities, and 52,527 of these emails reached the target while 3,118 were blocked by the security software, and 50,527 were not checked by recipients.
You can read the Keepnet 2021 Email Security Vulnerability Report in full here.





