Due to a bug in the Synapse app, a Razer mouse can cause anyone to have administrator permissions in Windows. Windows security has always been one of the workhorses of those who claim that the system is not as secure as it should be, and the truth is that they are right with news like this one, regarding a bug that allows obtaining administrator permissions when installing the drivers of a Razer wireless mouse.
A new vulnerability that does not require clicking on a suspicious file or installing a program from unofficial sources. A breach that puts the security of computers at risk and although, to exploit it, the attacker must have physical access to the computer, it still shows that Microsoft still has a lot of work ahead to improve the security of its system.
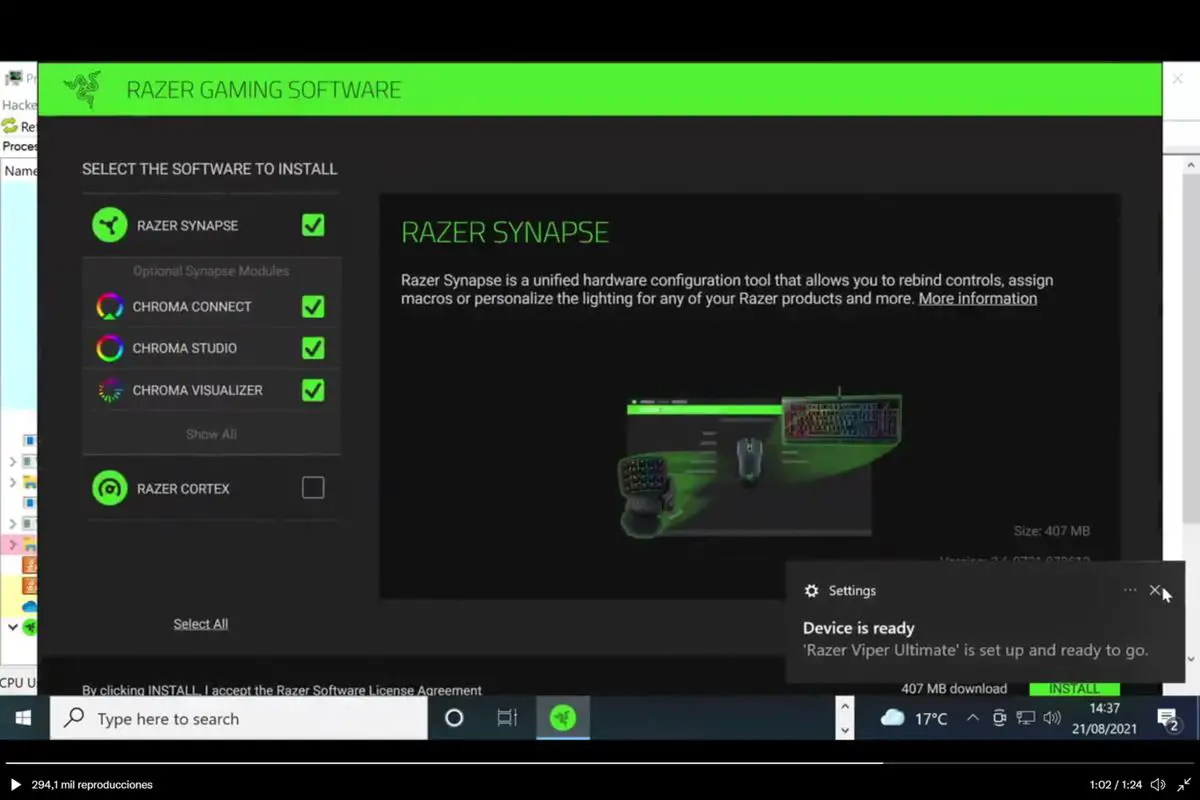
And in this case, the problem arises when installing the drivers for a Razer wireless mouse via the Synapse application. This is the tool that allows you to configure all the parameters as well as customize functions and controls to facilitate the use of, for example, a mouse and that benefits from the “Plug and Play” system that facilitates the connection of devices by simply “plugging” them into the PC.
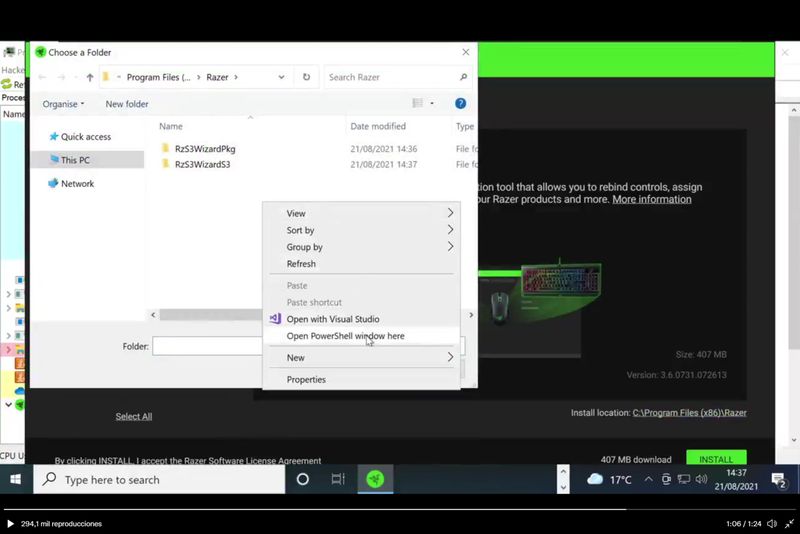
The Synapse application runs automatically when a Razer mouse is connected. Using the RazerInstaller.exe file, a normal installation is carried out, which however also allows the user to open an Explorer window to choose where to install the drivers. And this is where the problem begins, as the user can open PowerShell and access almost any function of the computer.
Need local admin and have physical access?
– Plug a Razer mouse (or the dongle)
– Windows Update will download and execute RazerInstaller as SYSTEM
– Abuse elevated Explorer to open Powershell with Shift+Right clickTried contacting @Razer, but no answers. So here's a freebie pic.twitter.com/xDkl87RCmz
— ҉j҉o҉n҉h҉a҉t҉ (@j0nh4t) August 21, 2021
The vulnerability has been discovered and published on Twitter by user @j0nh4t, who decided to make public the existence of this security breach after contacting Razer and getting no response at first. Following this article, Razer published a statement, stating that they are working on changes to the application to limit this use case.
The statement said: “We have become aware of a situation where our software, in a very specific use case, provides the user with broader access to their computer during the installation process. We have investigated the issue and are currently making changes to the installation application to limit this use case and will be releasing an updated version shortly. Use of our software (including the installation application) does not provide unauthorized third-party access to your computer.”
Exploiting this bug requires both a Razer mouse and personal access to the computer, two limits that minimize the impact of the breach but may leave us wondering how many such bugs can affect other “Plug & Play” devices.