The Microsoft team shared on Twitter the workings of a new ransomware campaign that has been endangering users for months.
Fake emails, phone numbers from an illegal call center and malicious code in Excel sheets are part of the strategy used by cybercriminals for this attack.
Microsoft’s cybersecurity team has been monitoring this threat, and details the steps cybercriminals are taking to trick users.
We're tracking an active BazaCall malware campaign leading to human-operated attacks and ransomware deployment. BazaCall campaigns use emails that lure recipients to call a number to cancel their supposed subscription to a certain service. pic.twitter.com/RS5wGSndhv
— Microsoft Threat Intelligence (@MsftSecIntel) June 22, 2021
We are tracking an active BazaCall malware campaign that leads to human-operated attacks and ransomware deployment. BazaCall campaigns use emails that entice recipients to call a number to cancel their supposed subscription to a certain service.
So it all starts with an email that “informs” the user that the trial period for a certain service is about to expire, and since the payment method is already registered they will proceed with the subscription.
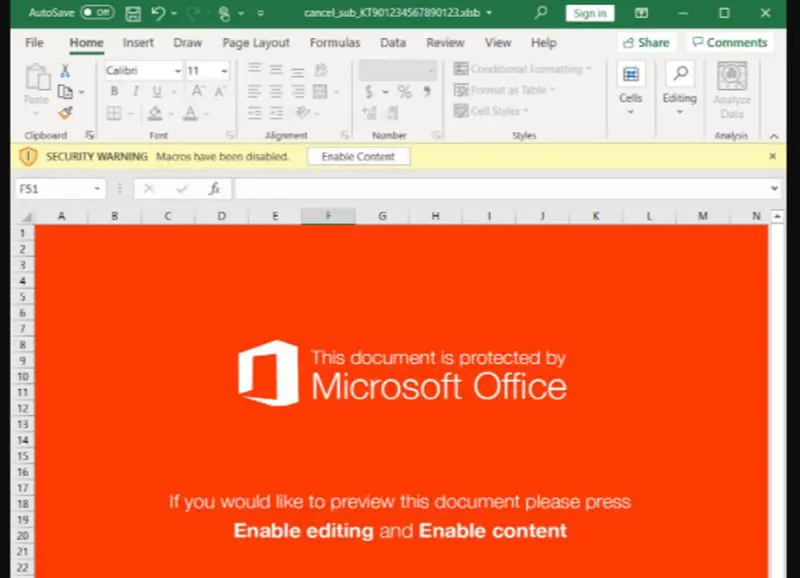
At this point, the user is nervous enough to call the phone number attached to the email, falling into the trap. Once they reach one of the phone numbers, they are asked to access a website and download an Excel file to cancel the subscription.
If the user follows all these steps and gets to the Excel file, they will notice that Microsoft launches a security warning, as you see in the image above. But if the user ignores this warning and enables the content, it results in the installation of malicious code and opens the doors of his computer to cybercriminals.
Most users trust that email services usually detect spam and threats, removing them from the inbox. However, as the Microsoft team mentions, these types of emails are difficult to detect, as they do not contain malicious elements that trigger the alarms of security systems.





