In this article we are going to vcover one of the worst SIM card scams there is: SIM swap. If your mobile is no longer covered, be afraid: a new phone fraud known as ‘SIM swapping‘ is being used so that a cyber attacker duplicates our phone number and uses that system to usurp our identity, authenticate ourselves in our bank and rob us all the money.
Twitter CEO has fallen victim to SIM card scams
There are already victims of a fraud that has been used for other purposes: Jack Dorsey, co-founder of Twitter, had his service account stolen with the same system, which once again highlights the weakness of mechanisms such as the SMS messages for two-step authentication systems. They were a good option originally, but as we said in the past, it is much more advisable to use independent authentication applications, and not the SMS that are increasingly vulnerable in this area.
What should you NOT do to prevent SIM card swap?
There are two clear problems here: first, that ordering a duplicate SIM is relatively straightforward . Second, that the use of SMS as a system to propose two-step or two-factor authentication (2FA) has long been vulnerable to various attacks, and this is only the last – but probably the most worrying – of them all. .
This technique makes it possible to circumvent the security measures that place the mobile as an instrument for verifying our identity, and that is dangerous as we have seen in the economic sphere, but also in many other scenarios.
We’re temporarily turning off the ability to Tweet via SMS, or text message, to protect people’s accounts.
— Support (@Support) September 4, 2019
It was demonstrated these days when Twitter co-founder and CEO Jack Dorsey suffered a similar attack that suddenly caused offensive and racist messages to appear on his Twitter account (@jack) that were later deleted.
SIM card swapping might result in identity theft
The problem was due to that identity theft that caused a phone operator in the United States – it is not specified which one – allowed the attacker to obtain a duplicate of Dorsey’s SIM, which in turn allowed this attacker to use the function of Posting on Twitter through SMS messages was one of the original features of the service.
The offensive messages sparked an immediate reaction from Dorsey, who announced that Twitter was disabling the delivery of messages to the platform via SMS.
Protect yourself against SIM swap: How to prevent SIM swapping?
Yhe problem with this cyberattack is that it has two widely separated faces, both with their own interdependent solution: if the two are not solved, the problem will continue.
The first is in those who handle that information, the operators, who should be much more demanding when it comes to providing duplicates of a SIM card. Identity checks here should be comprehensive to avoid the problems that have occurred with these cases.
Banks, financial institutions and any other platform that still uses SMS as a two-step authentication system also have pending duties. It is a popular and convenient method, but as we have seen it is very vulnerable for a long time, as pointed out by security expert Bruce Schneier. It is for this reason that all these companies should eradicate SMS from their authentication systems in two steps and use other alternatives.
Use 2FA / U2F against SIM swap attack
Among the most recommended right now are the authentication applications that replace SMS and can be installed on our mobiles. Microsoft Authenticator, Google Authenticator or Authy are among the best known, and if we can use them -the platform we work with must support that option- they are much more secure than authentication via SMS.

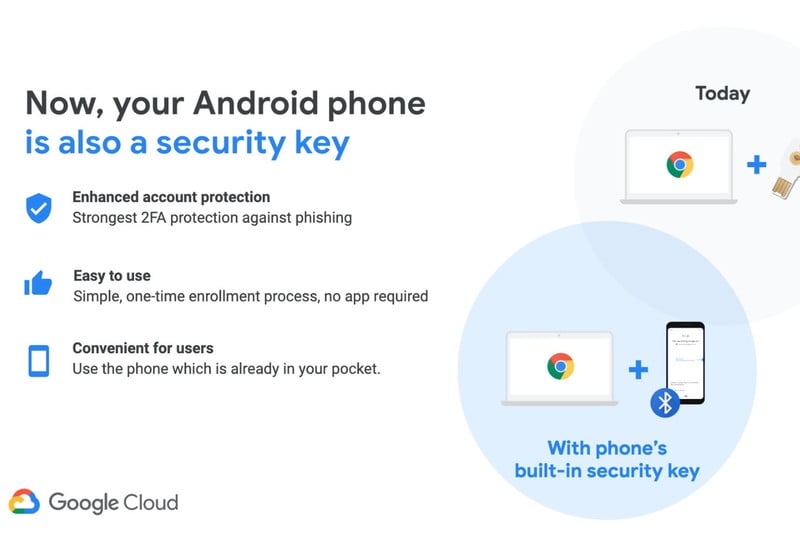
Even more interesting are the U2F keys (Universal 2nd Factor keys), an open authentication standard that makes use of physical keys and that has the FIDO2 standard as its last implementation . Manufacturers like Yubico are well known for these solutions, but even Google recently wanted to enter this segment with its Titan Security Keys , although it recently announced that an Android phone could also become a security key.





