The disclosure of a number of ongoing assaults against iPhones by the Russian cybersecurity company Kaspersky has brought Operation Triangulation to light. The campaign takes advantage of an iOS flaw and iMessage zero-click methods to install malware without requiring user engagement.
In an effort to counter this threat, Kaspersky has dubbed the operation “Operation Triangulation” and is inviting anybody with the knowledge to come forward and work with them.
This article explores the specifics of the campaign, its results, and the charges leveled by Russia’s FSB intelligence and security agency.

Operation Triangulation uses an iOS flaw
An investigation by Kaspersky indicates that iMessage zero-click attacks used by hackers to take advantage of an iOS vulnerability have been successful on iPhones linked to their network.
These methods allow the distribution of malicious code to the devices without involving the user. By taking advantage of this vulnerability, attackers can covertly download more malware from their servers.
Even if the original message and attachment are quickly deleted, a hidden payload with root rights is left behind, giving the attackers the ability to gather private data, issue remote commands, and keep persistence.
The trojan is thoroughly analyzed by Operation Triangulation
Kaspersky used the Mobile Verification Toolkit to analyze the virus in great detail in order to overcome the difficulties presented by iOS’s closed architecture. Important details about the assault procedure and the operation of the virus were discovered by generating filesystem backups of compromised iPhones.
Indicators of infection continue to exist despite the malware’s attempts to remove evidence of its presence. These include deprecated library injection, alterations to system files that prevent the installation of iOS upgrades, and unusual data consumption patterns.
Infection symptoms were first noticed in 2019, according to further analysis of the data gathered. Notably, iOS 15.7 was the most recent version of iOS to be targeted by this malicious toolkit, although iOS 16.5 was the most recent major update at the time of research. It is crucial to keep in mind that later iOS upgrades may have fixed the flaw that was exploited in these assaults, reducing the danger for devices running the most recent versions.
Websites linked to harmful behavior
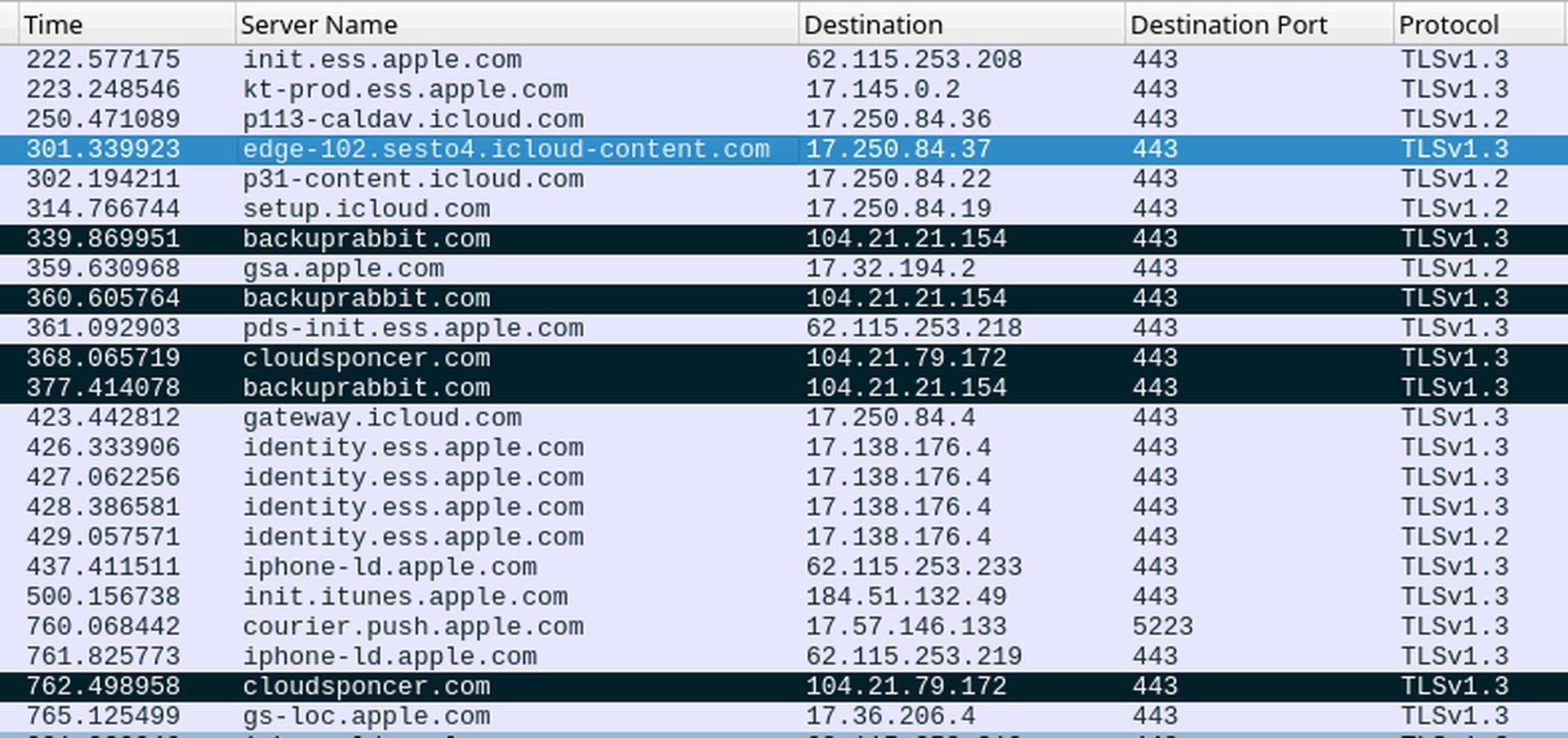
A list of 15 domains linked to the Operation Triangulation operation has been made available to security administrators by Kaspersky. Administrators are able to spot any exploitation on their devices by looking through old DNS logs.
As soon as the malware has more access, it downloads a full toolkit that gives the attackers control over the execution of instructions, the gathering of user and system data, and the retrieval of further modules from a command-and-control (C2) server.
It is important to note the lack of persistence capabilities in the APT toolkit employed in these assaults. Therefore, a quick device reboot efficiently stops the malware’s activity. Specific information regarding the malware’s capabilities is still scarce because the final payload’s study is still in progress.
Russia charges the US
In conjunction with Kaspersky’s findings, charges of cooperation between Apple and the NSA have been made by Russia’s FSB intelligence and security agency. According to the FSB, Apple knowingly gave the NSA a backdoor, allowing the NSA to infect Russian iPhones with malware.
They further claim that several hacked devices belonged to staff members from various embassies and members of the Russian government. The FSB hasn’t offered any hard data to back up these assertions, though.
The Russian state previously encouraged its presidential administration and government personnel to stop using Apple iPhones and stay away from American-made equipment. The effects of the assaults on Kaspersky’s Moscow headquarters and international staff members were confirmed.
However, the company made it clear that because it doesn’t have access to the government’s technical investigative information, it is unable to confirm a direct connection between its results and the FSB’s report. However, the Russian CERT has released a warning that ties the FSB’s assertion to Kaspersky’s results.
Are you into cybersecurity? Then you should check our article The Role of cybersecurity in compliance.





